Here’s everything you need to know to stay
safe when you’re online, wherever you are.
What’s on your Android phone? And more
importantly, how would you feel about that data being accessed by scammers,
hackers, and identity fraudsters. That’s exactly the risk uncovered by
Ralf-Philipp Weinmann, a researcher at the Luxembourg University who discovered
that he could listen to conversations, intercept data, and run up huge bills
calling and texting premium rate services – all without the alerting the
phone’s owner.
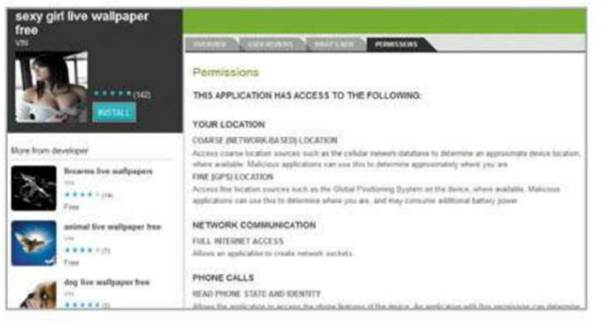
This
is a wallpaper app showing a fixed set of images, so why does it need your
location and full internet access?
With the ability to download and run apps,
smartphones are now the main focus for a growing number of malicious hackers,
and yet most devices are completely unprotected from such threats. For online
criminals, the situation resembles that of PCs in the mid-1990s, except they
now how much money there is to be made from online crime. Thanks to the deepest
recession in living memory, straightforward theft and street muggings for
smartphones are also at an all-time high, so how do you protect your freedom to
compute on the move?
Passwords first
Most people would never dream of using
something as obvious as 1234 as the password for their important online
accounts, but some users protect their smartphones with such a sequence and
then leave the online accounts it protects logged in for convenience.
Your first line of mobile defence should
always be to select a password that’s both memorable for you and difficult for
a theft to crack. For a few years now, the best advice on creating memorable
and secure passwords has been to take the initial letters of a line in a song,
poem, play or book, and to make a password from those letters. You can test the
strength of passwords you generate in this way by using free online web
security site services, such as How Big is Your Haystack at www.grc.com/haystack.htm.
As of version 2.2 Android OS supports not
only gesture passwords, but also the more traditional text-based variety. To
enable a password, click ‘Menu > Settings > Display’. You can combine a
password with gesture recognition, but always ensure that you use a gesture
that overlaps itself, otherwise the grease marks on the screen may give it away
to anyone who steals your phone. It’s also a good idea to clean the screen
every so often to prevent grit from scratching the gesture faintly into the
screen’s surface for posterity. To enable passwords, iPhone users should open
the Settings app and select ‘General > Passcode lock’. Windows Phone 7 users
should tap ‘Settings > Lock and wallpaper’, and BlackBerry users need to
select ‘Option > Security options > General settings.
Install antivirus
You would never dream of buying a laptop
and going online without installing at least a free antivirus product first.
The abilities of a smartphone or tablet computer are now approaching those of a
laptop, but it seems that the vast majority of users have no form of
protection, even though mobile computing devices are facing all the usual
threats. Spam containing malware attachments or links to attack sites, infected
apps and code that exploit operating system weakness are all beginning to appear.
Botnets made up of mobile devices are also becoming more common.

You
would never dream of buying a laptop and going online without installing at
least a free antivirus product first.
We’ve reached the point in the evolution of
mobile computing where it has become just as necessary to install antivirus
software on your phone as it is on every other online computing device. Most
antivirus vendors now offer free versions of their commercial mobile offerings,
and many offer handy package deals on their commercial versions, including
protection for multiple PCs and a phone, for a yearly subscription. It’s worth
investigating these deals because they could save you money in the long run,
but what’s the difference between free and commercial versions?
Mostly, the difference is down to the
facilities provided beyond basic protection. The ability to remotely wipe a
lost or stolen phone, for example, is something that will give you real peace
of mind, but it’s usually missing from the free versions of antivirus products.
Never be tempted to simply click a link
that looks OK and install what purports to be a free version of an antivirus
package. Check the URL; if it isn’t part of a vendor’s official website, don’t
visit the page. Fake antivirus software, written to infect your device or make
you think it’s protected when it’s not, has now made its way to smartphones. If
you’ve found a package on an app store, click through to be software vendor’s
website and download it from there.
Remote wipe
So you have a secure password guarding
immediate access to your phone, the screen lock activates after just a few
minutes of inactivity, and an antivirus package is watching out for any malware
in the background. However, if the worst happens and someone takes your
smartphone either by stealth or by force, you may also want to protect your
data by being able to wipe all your files and contacts quickly and remotely.

If
the worst happens and someone takes your smartphone either by stealth or by
force, you may also want to protect your data by being able to wipe all your
files and contacts quickly and remotely.
Android, BlackBerry and Windows Phone users
have a range of third-party, dedicated remote wipe applications to choose from,
which enable you to contact the phone and have it wipe itself. These tend to be
subscription services, but prices are usually less than $7.5 a month, which is
good value for extra peace of mind. Alternatively, you can examine the
facilities offered by different antivirus packages. Free versions, such as
AVG’s Mobilation Free, offer local wipe facilities. However, it’s not always
clear if remote wipe is included or just a local wipe facility, so check with
the software vendor before you part with your cash.
iPhone users can install Apple’s free Find
My iPhone app (www.bit.ly/tfERpz). This
gives you the ability to sign into another iOS device with your Apple ID,
locate the missing or stolen device, display a rather satisfying messages to
the robber, play a sound, lock the device and then erase it. The only proviso
is that your iPhone must have been enabled in the iCloud settings in order to
locate it.