User Account Control (UAC) represents a
significant change in the way user accounts are used and configured. It
affects which privileges standard users and administrator users have,
how applications are installed and run, and much more.
| Note |
Learning how UAC works will help you be a better
administrator. To support UAC, many aspects of the Windows operating
system had to be reworked. Some of the most extensive changes have to
do with how applications are installed and run.
|
Redefining Standard User and Administrator User Accounts
In Windows XP and earlier versions of Windows,
malicious software programs can exploit the fact that most user
accounts are configured as members of the local computer's
administrators group. Not only does this allow malicious software to
install itself, but it also allows malicious software to use these
elevated privileges to wreak havoc on the computer, because programs
installed by administrators can write to otherwise secure areas of the
registry and file system.
To combat the growing threat of malicious software,
organizations have locked down computers, required users to log on
using standard user accounts, and required administrators to use Run As
for performing administrative tasks. Unfortunately, these procedural
changes can have serious negative consequences on productivity. A
person logged on as a standard user under Windows XP can't perform some
of the most basic tasks, such as changing the system clock and
calendar, changing the computer's time zone, or changing the computer's
power management settings. Many software programs designed for Windows
XP simply will not function properly without local administrator
rights–these programs use local administrative rights to write to
system locations during installation and during normal operations.
Additionally, Windows XP doesn't let you know beforehand when a task
you are performing requires administrator privileges.
User Account Control seeks to improve usability while
at the same time enhancing security by redefining how standard user and
administrator user accounts are used. User Account Control represents a
fundamental shift in computing by providing a framework that limits the
scope of administrator-level access privileges and that requires all
applications to run in a specific user mode. In this way, UAC prevents
users from making inadvertent changes to system settings and locks down
the computer to prevent unauthorized applications from installing or
performing malicious actions.
Because of UAC, Windows Vista defines two levels of
user accounts: standard and administrator. Windows Vista also defines
two modes (run levels) for applications: standard user mode and
administrator mode. Although standard user accounts can use most
software and can change system settings that do not affect other users
or the security of the computer, administrator user accounts have
complete access to the computer
and can make any desired changes. When an administrator user starts an
application, her access token and its associated administrator
privileges are applied to the application, giving her all the rights
and privileges of a local computer administrator for that application.
When a standard user starts an application, her access token and its
associated privileges are applied to the application at run time,
limiting her to the rights and privileges of a standard user for that
application. Further, all applications are configured to run in a
specific mode during installation. Any tasks run by standard mode
applications that require administrator privileges are not only
identified during setup but also require user approval to run.
In Windows Vista, the set of privileges assigned to
standard user accounts has changed. Standard user accounts can perform
the following tasks:
-
Install fonts, view the system clock and calendar, and change the time zone.
-
Change the display settings and the power management settings.
-
Add printers and other devices (when the required drivers are installed on the computer or are provided by an IT administrator).
-
Download and install updates (when the updates use UAC-compatible installers).
-
Create and configure virtual private network
(VPN) connections. VPN connections are used to establish secure
connections to private networks over the public Internet.
-
Install Wired Equivalent Privacy (WEP) to connect
to secure wireless networks. The WEP security protocol provides
wireless networks with improved security.
Windows Vista also defines two run levels for
applications: standard and administrator. Windows Vista determines
whether a user needs elevated privileges to run a program by supplying
most applications and processes with a security token. If an
application has a standard token, or an application cannot be
identified as an administrator application, elevated privileges are not
required to run the application, and Windows Vista starts it as a
standard application by default. If an application has an administrator
token, elevated privileges are required to run the application, and
Windows Vista prompts the user for permission or confirmation prior to
running the application.
The process of getting approval prior to running
an application in administrator mode and prior to performing tasks that
change system configuration is known as elevation. Elevation enhances
security and reduces the impact of malicious software by notifying
users prior to performing any action that could impact system settings
and by preventing applications from using administrator privileges
without first notifying users. Elevation also protects administrator
applications from attacks by standard applications. For more
information on elevation and how UAC works with applications.
Optimizing User Account Control and Admin Approval Mode
Admin
Approval Mode is the key component of UAC that determines whether and
how administrators are prompted when running administrator
applications. The default way that Admin Approval Mode works is as
follows:
-
All administrators, including the built-in local administrator account, run in, and are subject to, Admin Approval Mode.
-
Because they are running in and subject to Admin
Approval Mode, all administrators, including the built-in local
administrator account, see the elevation prompt whenever they run
administrator applications.
In Group Policy under Local Policies\Security Options,
five security settings determine how Admin Approval Mode and elevation
prompting work. These security settings are:
-
User Account Control: Behavior Of The Elevation Prompt For Standard Users
Determines whether users logged on with a standard user account see an
elevation prompt when running administrator applications. By default,
users logged on with a standard user account are prompted for the
credentials of an administrator when running administrator
applications. You can also configure this option so users are not
prompted, in which case, the users will not be able to elevate
privileges by supplying administrator credentials. This doesn't prevent
users from right-clicking an application shortcut and selecting Run As
Administrator.
-
User Account Control: Switch To The Secure Desktop When Prompting For Elevation
Determines whether Windows Vista switches to the secure desktop before
prompting for elevation. As the name implies, the secure desktop
restricts the programs and processes that have application to the
desktop environment and in this way reduces the possibility that a
malicious program or user could gain access to the process being
elevated. By default, this security option is enabled. If you don't
want Windows Vista to switch to the secure desktop prior to prompting
for elevation, you can disable this setting. However, this makes the
computer more susceptible to malware and attack.
-
User Account Control: Run All Administrators In Admin Approval Mode
Determines whether users logged on with an administrator account are
subject to Admin Approval Mode. By default, this feature is enabled,
which means administrators are subject to Admin Approval Mode and
further subject to the elevation prompt behavior stipulated for
administrators in Admin Approval Mode. If you disable this setting,
users logged on with an administrator account are not subject to Admin
Approval and therefore are not subject to the elevation prompt behavior
stipulated for administrators in Admin Approval Mode.
-
User Account Control: Behavior Of The Elevation Prompt For Administrators In Admin Approval Mode
Determines whether administrators subject to Admin Approval Mode see an
elevation prompt when running administrator applications and also
determines how the elevation prompt works. By default, administrators
are prompted for consent when running administrator applications. You
can configure this option so administrators are prompted for
credentials, as is the case with standard users. You can also configure
this option so administrators are not prompted at all, in which case,
the administrator will not be able to elevate privileges. This doesn't
prevent administrators from right-clicking an application shortcut and
selecting Run As Administrator.
-
User Account Control: Admin Approval Mode For The Built-In Administrator Account
Determines whether users and processes running as the built-in local
administrator account are subject to Admin Approval Mode. By default,
this feature is enabled, which means the built-in local administrator
account is subject to Admin Approval Mode and further subject to the
elevation prompt behavior stipulated for administrators in Admin
Approval Mode. If you disable this setting, users and processes running
as the built-in local administrator are not subject to Admin Approval
and therefore not subject to the elevation prompt behavior stipulated
for administrators in Admin Approval Mode.
In a domain environment, you can use Microsoft Active
Directory directory service–based Group Policy to apply the desired
security configuration to a particular set of computers. You can also
configure these settings on a per-computer basis using local security
policy. To do this, follow these steps:
-
Click Start, All Programs, Administrative Tools, Local Security Policy. This starts the Local Security Policy console.
-
In the console tree, under Security Settings, expand Local Policies and then select Security Options, as shown in Figure 1.
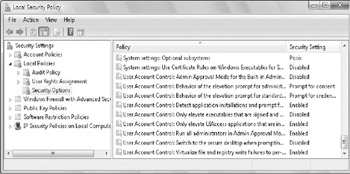
Figure 1: The Local Security Policy console.
-
Double-click the setting you want to work with,
make any necessary changes, and then click OK. Repeat this step to
modify other security settings as necessary.
|