This article is an introduction to
the special firewall distribution, IPCop.
In today’s world, dependence on the
Internet has reached such a level that without it, the day-to-day work of many
organizations will come to a standstill. As everybody is aware, when we connect
to the Internet, a public IP address is assigned, which is used to access the
Internet, and of course, can be used to track the actions from that IP address.
The Indian IT Act 2000 and its amendments make the IP address holder
responsible for all activities it has been used for. Thus, the management of a
company that has subscribed to the Internet connection is responsible for all
activities running on its IP address. This applies not only to the management
team members, but to all authorized and unauthorized users accessing the
Internet using that subscribed IP address.
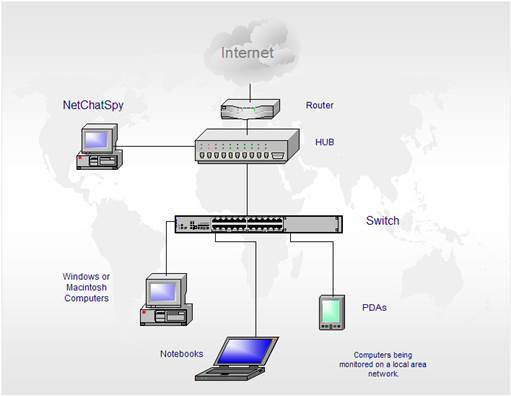
Basic
network
This 24x7 use of the Internet, business’
dependence on it, and emerging cyber laws have escalated the need to control
and monitor Internet access like never before. The first step towards
establishing this control is, of course, a network-based firewall. Please refer
to Diagram 1 for a typical example of an internal network connected to the
Internet using an ADSL router. Good and properly configured anti-virus
software, with a personal firewall, will meet the security requirements of most
individual users who connect to the Internet. However, for any organization
where multiple users on a network access the Internet, it is absolutely
necessary to look beyond these measures and opt for a network-based firewall.
Large corporations with IT security budgets
rely on commercially available firewalls for secure and controlled Internet
access. These security products can be put to use very effectively to restrict
Internet access, as per the company policy. However, they require continuous
investment – first to purchase and install the product, followed by yearly
renewals. For the management of small and medium-sized organizations, this may
be a luxury.
Operation
A typical network firewall is installed
between the internal network and the Internet; thus, all traffic between them
passes through the firewall. For Internet connections via an ADSL modem, the
firewall will be installed between the internal network and the ADSL modem,
whereas for an Internet connection with an Ethernet connection, the firewall
will replace the modem or router as depicted in Diagram 2. The firewall
analyses everything passing through, and based on the configured policy, let’s
through only ‘safe’ traffic.

A
typical firewall installation
Various client computer systems request
data from application servers simultaneously. A ‘port’ number is used to
differentiate this traffic. A client requesting data from the server uses the
destination port number of the corresponding service. For example, a computer
system requesting HTTP data will use port 80.
The traffic could use one of the following
two protocols:
·
Transmission Control Protocol (TCP), which
guarantees delivery of the data, is reliable but has larger headers to
accommodate the handshake signals and fags required for assured delivery.
·
User Datagram Protocol (UDP), which does not
guarantee delivery of the data, but has a smaller header. Here, higher-level
protocols may take care of assured delivery. Both TCP and UDP protocols have
65535 ports each. Ports up to 1024 are reserved.
A firewall uses
this port number to identify the traffic. In the HTTP example mentioned above,
the firewall reads HTTP traffic to port 80, and passes it to the Internet only
if it matches the desired policy. Unwanted websites and content as defined in
the policy will be dropped. Typical functions of a network firewall can be
classified into traffic control and others, as shown below.
Traffic control functions are:
·
Access from the Internet to the internal network
·
Website access from the internal network to the
Internet
·
Download of various file types such as
audio/video
·
Port-wise access from the internal network to
the Internet
·
Bandwidth control
Since all traffic between the internal
network and the Internet passes via the firewall, it is the best point to
provide various other functions such as:
·
A VPN gateway between two networks connected via
the Internet
·
A VPN server for remote clients connecting to
the internal network
·
Authentication of local users for Internet
access
·
Generation of traffic graphs
·
Logging Internet access
Why IPCop?
For a long time, the open source community
has provided many options for network firewalls by releasing various
distributions. They provide security and ease of configuration, and can be
installed on practically any minimal-configuration computer system. The most
important factor for SMBs is that these distros are free (under a GNU license)
and do not require yearly renewals. One of the best of these is the IPCop
firewall, which has a long history – it was forked from Smoothwall in 2001.
Various releases followed, the most popular being IPCop version 1.4.21 (the
last stable version available).

IPCop
1.4.21
The default v 1.4.21 had limited
functionality, but was flexible enough to allow installation of various add-ons
to enhance it to commercial-grade firewalls.
Installing IPCop with these add-ons
converts the basic distribution to a fully functional firewall, which also
includes free (and paid) updates for website blacklists. Installing add-ons
requires additional configuration work. Administrators used to face various
problems while installing, configuring and upgrading the add-ons. In
particular, taking back-ups of various add-ons' settings was cumbersome, since
IPCop's backup was only for the default settings (without add-ons). Also, new
computer hardware, especially most of the network cards, SATA hard disks and
flash drives were no longer compatible with IPCop 1.4.21.
IPCop Ver 2.0.x
The latest IPCop release, 2.0.x, addresses
these difficulties. It incorporates BOT, Zerina and AdvProxy add-ons. URL
Filter is also incorporated, but is expected to be fully functional in release
2.1. The latest release, as of January 1, 2013, is 2.0.6, which also includes
drivers for the latest computer hardware and supports installation on flash
drives as well.