New IE 7.0 Security Features
IE 7 has dozens of new security features. This section will not cover the dozens of other new features that have nothing to do with security (for example, tabbed browsing, RSS support, improved printing, search block, and so on). Here are the most significant security improvements:
-
Protected mode
-
Anti-phishing filter
-
Improved add-on management
-
Improved ActiveX control handling
-
Improved digital certificate handling
-
Improved encryption support
-
Improved URL handling protections
-
CardSpace
-
Parental controls
-
Privacy improvements
-
Pop-up blocking
-
Improved Cross Domain Scripting protections
-
Support for International Domain Names (used in a Firefox exploit in 2005)
-
RSS feeds automatically run in the Restricted sites zone
-
Larger minimum window sizes so that even at the smallest size, enough of the address bar and status bar are displayed to allow users to make trust decisions
-
Over a dozen new security options (covered in the material that follows)
-
Security status bar (easier and quick identification of Internet problems)
-
One-click Fix My Settings feature
-
Single-click browser content cache deletion
All of these improvements add up to a better and more secure Internet browsing experience. The next few sections cover the improvements with the biggest security impact.
Protected Mode
Oone of the most significant improvements to Vista is Internet Explorer's new Protected Mode. All security principals (for example, users, computers, groups, services, and so on) and objects (for example, files, printers, registry keys, and so on) are given a mandatory integrity ranking. The value can indicate low, medium, high, or system integrity.
All programs and applications run in the security context of a security principal (called impersonation or delegation). Most Windows system files (and most default Services) run in the Local System context. Most normal applications run in User mode, which means the application runs in the security context of the user who started it.
In Vista, when an application (with a given user's security context) attempts to access an object, both integrity levels are checked. If the program's security principal's integrity rating is equal to or greater than the object's integrity value, then it is possible for the security principal to write, modify, or delete the object, if the subsequent NTFS security permissions also allow it. If the security principal's integrity level is lower, the security principal will not be able to write, modify, or delete the object they are attempting to access regardless of the NTFS permissions. Integrity SIDs have precedence over NTFS permissions.
System objects are given the highest integrity rating of system. Most users and applications are given medium integrity by default. All normal Windows files and the desktop have medium integrity, but Internet Explorer running in Protected Mode runs with low integrity.
The idea is that even if a malicious program is able to "break out" into a system, if it originates from a low or medium integrity process, it will have a harder time modifying Windows system files than it would in previous versions of Windows. If malware successfully exploits Internet Explorer and then attempts to leverage that exploit into a further compromise of the system, as is common, the new integrity controls will make it much more difficult to accomplish.
For example, if Internet Explorer 7 is buffer overflowed, the malicious code will usually then attempt to install or modify files in the \System32 folder or startup areas (for example, HKLM\Software\Microsoft\Windows\CurrentVersion\Run registry key). Usually the hacker is attempting to install a backdoor program or to insert a malicious command and control program. Vista can prevent the subsequent modification, so that even though the initial exploit was successful, the overall outcome prevents the hacker from taking eventual control. To the hacker, it appears as if the exploit did not work at all.
| Note |
Although Windows XP Pro can run IE 7, it cannot run it in Protected Mode.
|
By default, IE runs in Protected Mode for most Web sites, and any process, child process, add-on, menu bar, and so on, related to it runs in low integrity. This is true even if the Administrator or an administrator-equivalent started IE. IE or any related process can only access low integrity locations by default without additional administrative confirmation.
New Low Integrity Folders and Registry Keys
Microsoft has created new "Low versions" of popular folder and registry keys. By default, low integrity locations intended for use by IE and its processes include:
-
\Users\%Userprofile%\AppData\Local\Temp\Low folder
-
\Users\%Userprofile%\AppData\Local\Temp\Low\Low folder
-
\Users\%Userprofile%\AppData\LocalLow folder
-
\Users\%Userprofile%\Local Settings\Temporary Internet Files\Low folder
-
\Users\%Userprofile%\Local Settings\Temp\Low folder
-
\Users\%Userprofile%\Local Settings\Temp\Low\Low folder
-
\Users\%Userprofile%\Local Settings\History\Low folder
-
\User\%\Userprofile%\Local\Temp\Low folder
-
\Users\%Userprofile%\AppData\Local\Microsoft\Windows\Temporary Internet Files\Low folder
-
\Users\%Userprofile%\AppData\Local\Microsoft\Windows\History\Low folder
-
*\Users\%Userprofile%\AppData\Roaming\Microsoft\Windows\Cookies\Low folder
-
HKLM\Software\Microsoft\Internet Explorer\Low Rights registry hive
-
HKCU\Software\Microsoft\Internet Explorer\LowRegistry registry hive
Essentially, a low integrity program can write to any low integrity area or object in Windows (if NTFS permissions also allow it), plus IE can write to any file or content it creates in those low integrity areas.
| Note |
The Low integrity folders vary system to system, and there are certainly going to be more Low integrity folders than are listed previously. Additionally, newly added applications can add their own application-specific folders.
|
Internet Explorer 7 is in Protected Mode by default for all security zones except the Trusted Sites zone. IE 7 displays whether or not it is in Protected Mode on the status bar (see Figure 1). Protected Mode can be turned off in the Internet Explorer Internet Options dialog box for each zone (see Figure 2), or using group policy.
In previous versions of IE, if the logged-in user was an Administrator (which was often the case), malware exploiting Windows could exploit the user's system. IE Protected Mode complicates the job of viruses, worms, Trojans, adware, and spyware when they're trying to hijack the user's computer.
IE Compatibility Shims
Of course, users and developers need a way to install legitimate programs and content. Microsoft allows this using a new shim compatibility architecture. By default, a program or process spawning from IE can access only low integrity resources. If they try to access objects with higher integrity, they will be denied.
However, if a program or process attempts to write to a medium integrity object, such as the HKCU\Software registry hive or the user's My Documents folder, Windows will redirect registry writes to:
HKCU\Software\Microsoft\InternetExplorer\  InternetRegistry\REGISTRY\USER\{user's SID}\Software
InternetRegistry\REGISTRY\USER\{user's SID}\Software
and the file writes to
User\%UserProfile%\AppData\Local\Microsoft\Windows\ 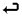 TemporaryInternetFiles\Virtualized\{system drive
TemporaryInternetFiles\Virtualized\{system drive  letter}\Users\{username)
letter}\Users\{username)
Programs, legitimate or not, can request access to higher privileged objects using two new broker processes:
Ieuser.exe runs with medium integrity and Ieinstal.exe runs with high integrity. Processes running under either broker are subject to normal registry and file virtualization rules, and will be further protected by Data Execution Prevention (DEP). When a user intentionally downloads a file, Ieuser.exe will participate in the downloading of the file. The downloaded file and the process will be marked with medium integrity. Manually initiated install processes will run with high integrity.
IE will either automatically call these additional, elevated broker processes when needed, and Microsoft allows developers to access higher levels of integrity through a variety of programmatic means. Most require that the installing user approve the action. Figure 3 shows an example dialog box.
| Note |
Interestingly, although Ieuser.exe and Ieinstall.exe are protected by DEP, 32-bit versions of Iexplore.exe are not (64-bit versions are protected by DEP), making IE still susceptible to many common buffer overflow types.
|
| Note |
It important to realize that files manually downloaded or installation/setup routines initiated by a user will use the elevated processes of Ieuser.exe or Ieinstal.exe. Bypassing IE's Protected Mode is as simple as convincing the user to download or run a file. IE's Protected Mode is designed to make downloads and installs without the user's consent (i.e. "drive-by-downloads") harder to pull off for the malware writer.
|
Protected Mode's Impact on Malware and Hackers
It is interesting to note that Microsoft has documented how developers can use compatibility shims and brokers to elevate integrity levels of their programs or communications. Microsoft even possibly allows a newly installed program to modify the registry in such a way that the program can elevate itself to a medium integrity or communicate to a medium integrity process without warning the user (see http://www.msdn.microsoft.com/ie/default.aspx?pull=/library/enus/IETechCol/dnwebgen/ProtectedMode.asp). So, just like before, in previous versions of Windows, the user's decision to run or install any program can allow the program to do more than the user originally intended.
| Note |
Although there is documentation discussing how an application can "silently elevate" itself, the functionality does not appear to work. The authors hope that the feature documented previously is never implemented.
|
The impact of Protected Mode on IE's overall security is yet to be tested thoroughly. Three major issues loom. First, as covered above, 32-bit versions of Iexplorer.exe (i.e. the main Internet Explorer) executable does not run with DEP protection, which means IE is still susceptible to many common types of buffer overflows. Microsoft was forced to initially exclude 32-bit versions of IE from DEP protection because many popular IE legacy add-ons, including Adobe, Flash, Active Type Library, and Sun's Java Virtual Machine (JVM), will cause fatal error problems. When operational problems occur, regardless of the reasons, many end users will blame Microsoft and not the add-on vendor. They will not be understanding of Microsoft's need to develop a more secure browser, so Microsoft has to ensure a moderate level of backward compatibility.
Second, if the user can be tricked into downloading a file or running a malicious executable, that file will be downloaded or executed with elevated integrity, bypassing one of the strongest IE-PM protections.
Third, it's excellent that Microsoft block writes to critical system areas. However, it is likely that new threats will be able to accomplish historical types of maliciousness by using only the low integrity areas.
Luckily, in many instances, Vista's separation of privileges will prevent one user's mistake from infecting the whole system. But if malware is able to leverage a user's low integrity areas, they can at least maliciously interact with that user. If the computer is only used by a single user it doesn't really matter whether the malware attacked only one user's profile or the whole system. However, if malware is prevented from manipulating trusted system areas, it is a huge advantage and means detection and removal tools can be more accurate. Whether malware can break out of Protected Mode and infect the whole system is a tougher problem for malware writers to solve. Unfortunately, if past history is any guide, worm and Trojan creators will eventually figure out a way to circumvent IE's Protected Mode. Although IE 7-PM is significantly previously secure than previous versions, it is likely that the weaknesses mentioned above, and other newly discovered vulnerabilities, will mean that IE 7 remains a frequent hacker target of success.
Anti-Phishing Filter
E-mail phishing attacks have become a huge security problem. A phishing attack involves ending a realistic, but fraudulent e-mail to an unsuspecting end user asking for confidential information (usually logon information, passwords, or financial information). Over the years, phishing e-mails have become so legitimate looking that they are hard for the novice to identify. See http://www.antiphishing.org for more phishing details.
IE 7 has new intelligence to scan all incoming Web content looking heuristically for signs that might indicate a malicious phishing Web site. By default, IE will check with Microsoft on every incoming Web site URL in all zones except the Trusted Sites to see if it has been previously reported as a malicious Web site. If it identifies a previously reported and confirmed phishing Web site, it will declare the Web site as a known phishing site and block the access (see Figure 4). If the Web site has not been reported, but still appears suspicious, IE 7 displays a gold warning bar (see Figure 5).
While IE 7's anti-phishing filter isn't extremely accurate (it suffers from a fair amount of false-positives and false-negatives), it is a nice added feature to the IE family. Users can report any Web site to Microsoft as potentially malicious (see Figure 6), and Microsoft will verify the site's intent before adding it to their database as malicious. Users have to type in the correct, obscured letters (see Figure 7) to successfully report a suspected phishing Web site. This is to prevent Phishers from submitting thousands of legitimate sites programmatically to decrease the accuracy of Microsoft's databases.
Add-on Management
Insecure Add-ons (i.e., Browser Helper Objects and extensions) have been responsible for many of the IE security vulnerabilities. To that end, Microsoft has made it much harder for any Add-on to modify Internet Explorer without a user's permission (for example, UAC, Protected Mode), and a user can more easily manage and disable current Add-ons.
Add-on management is accessed through the Tools, Manage Add-ons, Enable or Disable Add-ons IE menu choices. By default, the Add-ons currently loaded in IE will be displayed (see Figure 8), both the enabled and disabled programs. You can also use the new Manage Add-on option box to show all previously loaded Add-ons. It can also show Add-ons requiring permissions to run, and all the previously downloaded and installed ActiveX controls.
You can run Internet Explorer without any active add-ons by clicking the Start button, and then choosing All Programs, Accessories, System Tools, and then clicking on Internet Explorer (No Add-ons). You can run IE7 in Windows XP without add-ons by right-clicking Internet Explorer's icon or executable and selecting Start without Add-ons.
When IE 7 starts it checks the list of installed Add-ons. Previously identified Add-ons that cause stability or security problems will be prevented from loading by default. The user will be prompted to enable, disable, or check for updated versions (see Figure 9).
Improved ActiveX Control Handling
Insecure ActiveX controls have been responsible for many buffer overflows and privilege escalation attacks. IE 7 disables all ActiveX controls that were not previously used in IE 6. When a user runs an ActiveX control for the first time on the Internet or in Restricted sites zones, they will see a warning bar asking to approve the control. The ActiveX Opt-in policy does not apply to the Intranet and Trusted Sites zones, or to any controls previously approved by the Administrator or through group policy.
Improved Digital Certificate Handling and Encryption
A HTTPS protected web page ensures that the Web site is authenticated (that is, it is who it says it is) and that all communications between the server and the client are encrypted. HTTPS is an Internet standard and supported by most browsers and commercial Web sites.
HTTPS and digital certificates work well if the users pay attention to the errors and warning messages from invalid sites and certificates, which is not usually the case. IE 7 is more "in your face" with site and certificate errors. If an HTTPS Web site has a digital certificate error, IE 7 warns the user, gives exact details for the warning, and refuses to display the page by default (see Figure 10). The user can click the warning message for more details, close the page attempt, or continue on. Additionally, elevation is needed to permanently install any remote Web site's digital certificate.
IE 7 is doing its part to engage users to pay attention and to increase the security of HTTPS at the same time. First, weaker SSL ciphers (40-bit and 56-bit) have been disabled by default. Vista now supports 128-bit and 256-bit SSL encryption routines. The older and weaker SSLv2 protocol has been disabled by default. SSLv3 and the even stronger TLS routines have been enabled by default.
Digital certificate revocation is enabled by default. Certificate revocation occurs when an issuing Certification Authority or the digital certificate it issued becomes compromised. If a digital certificate is revoked, it should be considered untrustworthy. In IE 6, certificate revocation was optional, but improved support for the OCSP protocol allows Microsoft to have confidence when turning it on. Last, HTTP content attempting to post inside a HTTPS page (called mixed content) is blocked by default. IE 6 just warned. Some Web sites use mixed content, but doing so is normally considered a security vulnerability.
By disabling weaker ciphers, enabling better encryption protocols, and blocking sites with certificate problems, essentially Microsoft is telling Web site developers to get up to date on their security. Only time will tell whether or not HTTPS and digital certificates will truly lead to better, improved security.
Improved URL Handling Protections
IE 7 will no longer render URLs that do not meet RFC guidelines. Many phishing and spam e-mails, and hacker attacks, use malformed and encoded URLs to initiate their maliciousness. IE 7 has been specifically coded to ignore and drop suspiciously encoded URLs and other devious strings. (For example, %25 in URL paths will no longer be decoded to %, stopping many obscurity and directory traversal attacks.) The common directory traversal string ../../../../../ doesn't work anymore. Improved URL handling protects end users and also vulnerable Web sites.
CardSpace
Windows CardSpace is Microsoft's new method for delivering logon credentials and other information (for example, credit card numbers, personal identity information) to participating Web sites and network resources. Users create individual "cards" (see Figure 11), which can then be securely transmitted to requesting sites. It is a user-centric, user-managed identity management space. When creating and transmitting cards, CardSpace becomes the focus while the UAC mechanism prevents malicious interactions on the local computer. Many people believe that CardSpace is a replacement for Microsoft's Passport mechanism. CardSpace will probably replace Passport, but operates differently and can do much more. There is a great wiki discussion on CardSpace located at http://www.en.wikipedia.org/wiki/Windows_CardSpace.
| Note |
CardSpace is also available in Windows XP if .NET Framework 2.0 or later is installed.
|
The previous sections explored the biggest changes between IE 7 and IE 6.
|