To help make the operating system more secure,
Internet Explorer security was revised greatly starting with Windows XP
Service Pack 2, and these same changes are in Windows Vista. These
security changes affect many areas of the browser and introduce several
new features, including:
The sections that follow examine each of these features.
Understanding Dynamic Security Protection, the Browser Information Bar, and Other Browser Security Enhancements
Dynamic Security Protection in Internet Explorer
is a comprehensive safety and security framework designed to safeguard
the integrity of your organization's computers while also helping to
protect an individual's personal information. The main features of
Dynamic Security Protection are Protected Mode, privacy reporting, and
phishing filter.
Protected Mode isolates Internet Explorer from other
applications running on the computer and restricts how adds-ons are
used. Because of Protected Mode, add-ons can only write information to
temporary Internet folders and must have explicit consent from the user
to write to any other location. Additionally, preinstalled Microsoft
ActiveX controls are disabled by default, and you can start Internet
Explorer with all add-ons disabled if desired. To start Internet
Explorer in Add-On Disabled mode, click Start, All Programs,
Accessories, Internet Explorer (No Add-Ons), or right-click the
Internet Explorer shortcut on the desktop and select Internet Explorer
(No Add-Ons).
As part of the Protected Mode enhancements, the URL
handler in Internet Explorer has been redesigned as well. The updated
URL handler has a new parser, which protects the computer from possible
URL parsing exploitations, such as URLs that attempt to run commands.
This new parser also features international domain name anti-spoofing,
which is designed to warn users if malicious individuals use the new
international domain name support to create look-alike domain names.
Privacy reporting provides quick access to privacy
information that includes whether cookies were restricted or blocked
based on privacy settings; which Web sites have content on the page;
and the accepted, restricted, or blocked status of cookies from those
sites. In Internet Explorer, you can view a privacy report for the open
page by clicking Page and then clicking Web Page Privacy Policy.
Phishing is a technique whereby a site attempts
to collect personal information without a person's consent. Internet
Explorer's phishing filter warns you about sites known to collect
personal information without consent and also displays a warning when a
site attempts to collect personal information without your consent.
Related warning icons are displayed on the browser's status bar. With
the status bar warnings, however, it is important to keep in mind that
the warning doesn't necessarily mean a site conducts or is conducting
phishing. Instead, it might only mean that the site isn't a large,
wellknown, commercial site.
The Phishing Filter is always on by default. In
Internet Explorer, you can manage the phishing filter by clicking Tools
and then clicking Phishing Filter. If you select Turn Off Automatic Website Checking, you can manually check sites if desired using the Check This Website option.
In Windows Vista, the Browser Information Bar is used
in place of many of the common Internet Explorer dialog boxes and
prompts. The information bar is designed to help users navigate the
many security enhancements for pop-up windows, add-ons, and active
content. When the information bar is displayed, it appears just below
the address bar. Whenever this bar is displayed, you can click or
right-click it to display a shortcut menu with additional options that
allow you to enable or disable the related feature and perform other
related tasks.
Table 1 provides a summary of the most common messages you'll see and the related options in the Internet Properties dialog box.
Table 1: Understanding Secure Browsing and Lockdown
|
Information Bar Message
|
Description
|
Action/Resolution
|
|
Active Content Blocked. To help protect your
security, Internet Explorer has restricted this file from showing
active content that could access your computer.
|
This message is displayed for any pages that
contain scripts or other types of active content that access
information on the local computer. Active Content is blocked by default
to ensure malicious files accident.
|
You can configure active content blocking by
selecting or clearing Allow Active Content To Run In Files On My
Computer on the Advanced tab of the Internet Properties dialog box. To
allow only this particular page to execute active content, click the
information bar. Active content on CD AutoRun pages can be controlled
using Allow Active Content From CDs To Run On My Computer.
|
|
File Download Blocked. To help protect your
security, Internet Explorer blocked this site from downloading files to
your computer.
|
This message is displayed any time an automatic
download or installation is prevented. Downloads are blocked by default
to prevent sites from overwhelming users with download prompts and to
help resolve problems with accidentally installing unwanted software.
|
You can configure automatic prompting through the
Web zone security settings. On the Security tab of the Internet
Properties dialog box, select a Web zone by clicking it and then
clicking Custom Level. In the Security Settings dialog box, select the
appropriate option for Automatic Prompting For File Downloads. To allow
only the blocked file to download, right-click the information bar and
select Download Software.
|
|
Pop-up Blocked. To see this pop-up or additional options, click here…
|
This message is displayed whenever a page contains a link that opens a new window or a script calls a method, such as window.open(), that opens a new window, and the Pop-up Blocker is in effect.
|
You can configure the blocking of pop-ups by
selecting or clearing Block Pop-Ups on the Privacy tab of the Internet
Properties dialog box. To configure pop-up blocking exceptions, click
Settings on the Privacy tab and set a specific exception. You can also
configure an exception for the current site by right-clicking the
information bar and selecting Allow Pop-Ups For This Site.
|
|
Software Install Blocked. To help protect your
security, Internet Explorer stopped this site from installing software
on your computer.
|
As with drivers, digital signatures are checked
before downloading and installing ActiveX controls and other
executables. This message is displayed whenever you attempt to install
an ActiveX control or other executable with a missing or invalid
signature. In general, it is a good idea to block these downloads
because they are typically from untrusted publishers and might also
represent malicious or undesirable types of files, such as adware.
|
You can configure the blocking of executables by
selecting or clearing Allow Software To Run Or Install Even If The
Signature Is Invalid on the Advanced tab of the Internet Properties
dialog box. To allow only this executable to install, right-click the
information bar and select Install Software.
|
|
Software Blocked. Your security settings do not
allow ActiveX controls to run on this page. This page might not display
correctly.
|
This message is displayed if running of ActiveX controls and plug-ins is disabled or blocked by an administrator.
|
You can configure the way ActiveX controls and
plug-ins run by setting Web zone security settings. On the Security tab
of the Internet Properties dialog box, select a Web zone by clicking it
and then clicking Custom Level. In the Security Settings dialog box,
select the appropriate option for Run ActiveX Controls And Plug-Ins. To
allow ActiveX controls and plug-ins only for the current site,
right-click the Information Bar and select Allow This Site To Run
ActiveX Controls.
|
Using the Add-On Manager for Internet Explorer
Internet
Explorer functionality can be extended and enhanced through add-ons.
Many types of add-ons are available, including the following:
-
Browser helper objects that add help dialog boxes and other help information
-
Browser extensions that add functionality or enhance browser features
-
Toolbar options that add menu items and buttons to the browser toolbar
-
ActiveX controls that provide additional
functionality and allow execution of additional types of media such as
Shockwave Flash files
As Figure 1
shows, these and other types of add-ons can be controlled through the
Manage Add-Ons dialog box. To access this dialog box, access the
Internet Properties dialog box and then click Manage Add-Ons on the
Programs tab. You can then use the following options:
-
Enable add-ons To enable an add-on that has been
disabled previously, select it and then click Enable. If the option is
unavailable (dimmed), the Do Not Allow Users To Enable Or Disable
Add-Ons policy might be enabled in Group Policy under User
Configuration\Administrative Templates\Windows Components\Internet
Explorer.
-
Disable add-ons To disable an add-on, select it and
then click Disable. Internet Explorer Crash Detection enables users to
disable add-ons that cause problems with the browser. You can control
Crash Detection using the Turn Off Crash Detection policy under User
Configuration\Administrative Templates\Windows Components\Internet
Explorer.
-
Update add-ons If an ActiveX control is known to
have an update available (as determined by Automatic Updates), you can
select the add-on and click Update ActiveX to update the add-on.
| Real World |
Because Windows Vista includes a built-in pop-up
blocker, pay particular attention to any browser add-ons that act as
pop-up blockers. Many Internet service providers (ISPs), Earthlink
included, provide pop-up blockers to their customers. Some firewall and
antivirus software includes pop-up blockers as well. Running a third
party pop-up blocker in addition to the Windows pop-up blocker can lead
to results that can be very confusing. Typically, you'll want to use
only the Windows pop-up blocker and disable any other pop-up blockers
running on the computer. In most cases, you'll find the Windows pop-up
blocker is more configurable than other pop-up blockers, and it's
easier to work with as well.
|
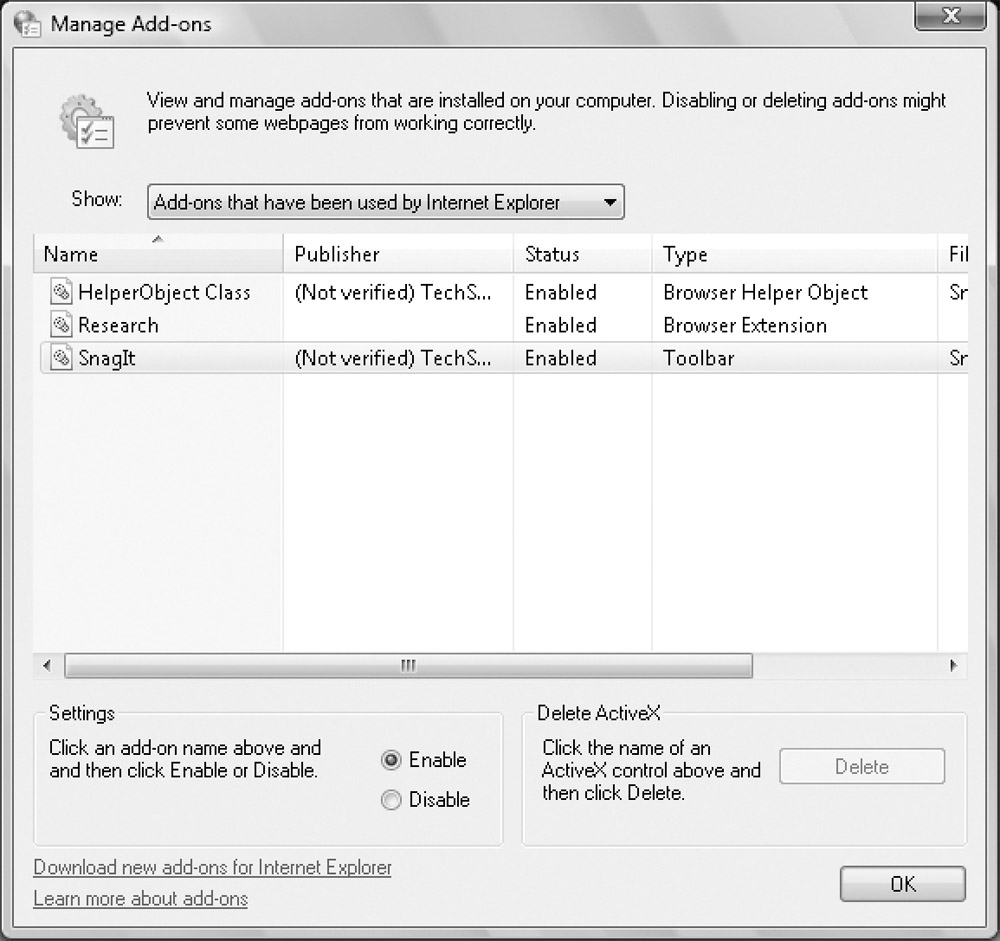
Figure 1: ActiveX controls and other browser add-ons can be enabled, disabled, or updated using the Manage Add-Ons dialog box.
Configuring the Pop-Up Blocker
Many Web pages contain pop-ups, which are subwindows typically displayed by a call to the window.open() method in a script. Some examples of how pop-ups are created include the following:
-
A hypertext link contains a command that opens a window when it is clicked.
-
A page element contains a command that opens a window when it finishes loading.
-
A script in a page opens a window after a function call.
Because many pop-ups are ads or are otherwise unwanted,
Windows Vista includes the Pop-Up Blocker feature. By default, Windows
Vista is configured to block most types of automatic pop-ups and
display the Information Bar whenever pop-ups are blocked. A user could
then right-click the Information Bar and select Allow Pop-Up to display
the pop-up or right-click the Information Bar and select Allow All
Pop-Ups For This Site to configure the site as an Allowed Site
automatically, which unblocks (or allows) pop-ups from this site.
You can configure pop-up blocking by completing the following steps:
-
Access the Internet Properties dialog box in
Control Panel by clicking Network And Internet and then clicking
Internet Options. Then select the Privacy tab.
-
To disable pop-up blocking, clear Turn On Pop-Up Blocker and then click OK. Skip the remaining steps.
-
To enable pop-up blocking, select Turn On Pop-Up
Blocker and then click Settings. This displays the Pop-Up Blocker
Settings dialog box, shown in Figure 2.
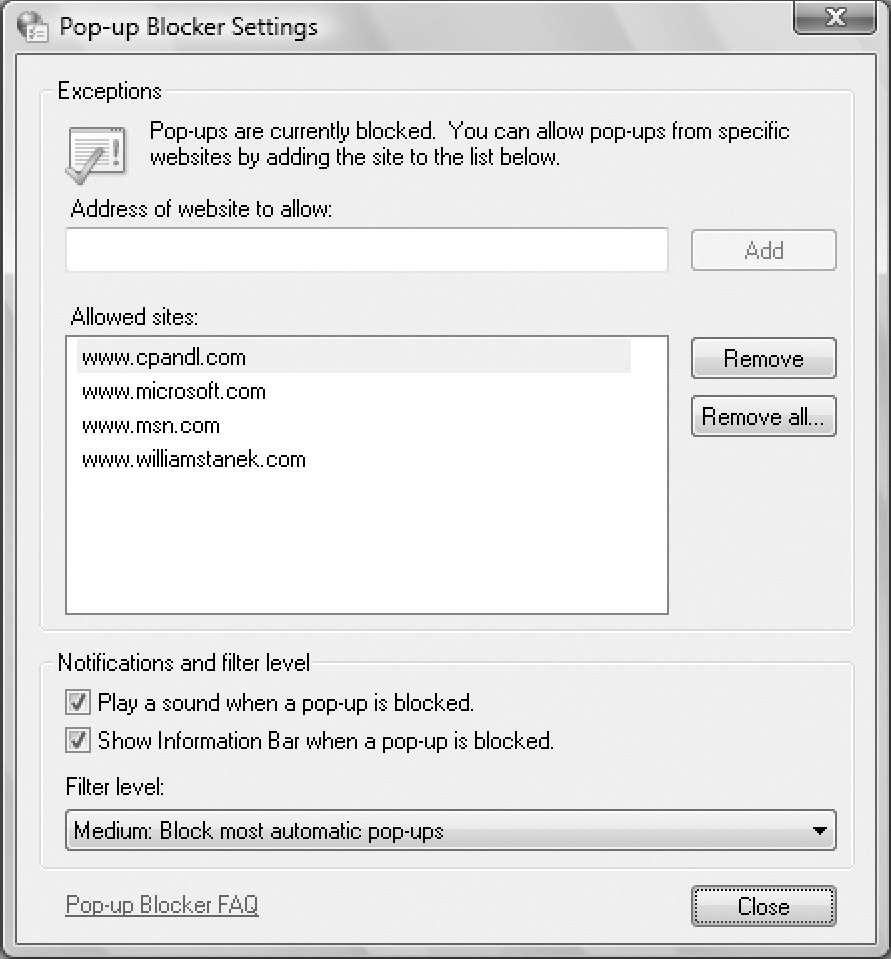
Figure 2: Use the Pop-Up Blocker Settings dialog box to configure the way pop-ups are blocked.
-
To allow a site's pop-ups to be displayed, type the address of the site in the field provided, such as http://www.msn.com, and then click Add. This site is then permitted to use pop-ups regardless of Internet Explorer settings.
| Tip |
By default, Pop-Up Blocker is disabled for sites
in the Local Intranet zone. That said, you still might want to
configure exceptions for internal sites if these sites call the window.open()
method in scripts or use similar methods to open windows. In this way,
you ensure pop-ups for internal sites aren't blocked, regardless of the
browser settings. You can also configure exceptions through the Pop-Up
Allow List policy under User Configuration\Administrative
Templates\Windows Components\Internet Explorer.
|
-
To stop displaying an information message in the
browser when pop-ups are blocked, clear Show Information Bar When A
Pop-up Is Blocked.
-
By default, most types of automatic pop-ups are
blocked when the Pop-Up Blocker is enabled. You can use the following
options of the Filter Level selection menu to control the types of
pop-ups that are blocked:
-
q High: Block All Pop-Ups (Ctrl+Alt To Override)
Pop-up blocker attempts to block all pop-ups. If you click a link that
would normally open a pop-up and you want to see the pop-up, press
Ctrl+Alt while clicking to open the pop-up.
-
q Medium: Block Most Automatic Pop-Ups
Pop-up blocker attempts to block the types of pop-ups most commonly
used to display ads or other unwanted content. Some types of new
windows are allowed. Again, you can press Ctrl+Alt to override blocking
while clicking a link.
-
q Low: Allow Pop-Ups From Secure Sites
With standard (HTTP) connections, Pop-Up Blocker attempts to block the
types of pop-ups most commonly used to display ads or other unwanted
content. However, Pop-Up Blocker allows pop-ups when you are accessing
a site using a secure (HTTPS) connection.
-
Click Close and then click OK.
|