Protect yourself
So what can we do? The Communications Data
Bill is yet to be passed as law, so contacting your MP could be a good place to
start. In fact, getting as many people as possible to contact their MPs would
be a better place.
A more immediate solution is to ensure that
you and anyone else who uses your computer is aware that the data they put
online is not private. Also use tools such as Collusion to monitor who is
watching you.
You can change your browser’s security
settings to stop these cookies being stored in the first place, and regularly
clear out the history and cookies to remove those that slip through the net.
Limit the use of location services, resist clicking the ‘Like’ button, and even
use a different browser for all interaction on social networks.
The more cautions could boot a Linux
operating system from a USB flash drive when using public Wi-Fi, or download
Wi-Fi Guard from AVG.
In the end, though, the most potent weapon
we can use against those who would try to profit from tracking us is an
awareness of what might be happening.
The internet is growing up and maturing
into a stunningly powerful tool and an amazing place to explore. Like any great
adventure, there are a few dangers to negotiate along the way.
We shouldn’t let the fear of a Big Brother
state or shadowy data brokers deny us the advantages of services such as Google
and Facebook, and if we’re careful to limit the important data we share then we
should be able to protect ourselves in some measure.
Ryan Merkley sums it up rather well: “A
no-tracking universe probably isn’t the answer. We want users to be informed
and in control of their web experience: the more they know, the less likely
anyone can track them without their knowledge. Informed and empowered users has
always been the best thing for the web.
In with the out crowd
If you’re ever thought about quitting a
service such as Facebook then you’ll realise just how big a decision that
actually is. Google has heavily promoted its Google+ service, but struggled to
draw the kind of numbers needed to make it a serious rival.
Primarily, this is because most people who
would ever use a social network are already using Facebook; more importantly,
so are their friends. Who really has the time to update two or three social
network and, even if you did, what’s the point?
If the privacy compromises associated with
either social network have so far but you off signing up and catching up with
long-lost friends and family, several alternative options are available –
provided you can convince your friends to sign up too.
Diaspora is one of a new breed of social
networks that belong to the users; its decentralized network means no-one holds
all the information. Instead, the site works via social pods that join together
to form the network. The service also allows you to link your Facebook,
Twitter, or Tumblr account and still chat with your existing friends. Although
it’s invite-only at the moment, it shows promise for the future.
Another independent site worth checking out
is Friendica. F coffers many of the same features as Diaspora, but adds some
interesting ideas, such as content automatically expiring after a given period
of time and the ability to create posts of unlimited length. Bloggers should be
happy here.
Chrome privacy
Changing
your settings in Google’s Chrome web browser is easy. Simply open Chrome, click
the spanner icon, then choose Settings. Scroll down to and click ‘Show advanced
settings’ to reveal the Privacy menu. 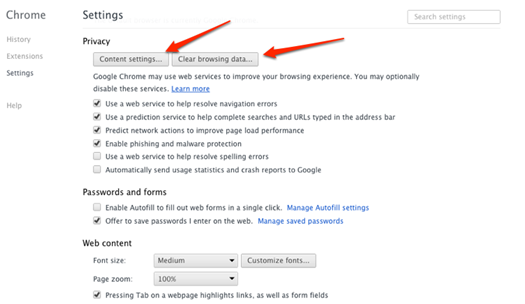
Chrome
privacy
Ensure that the ‘Enable Phishing and
Malware protection’ box s ticked, then click the Content Settings button. Leave
alone the Cookies setting, but be sure to enable ‘Block third-party coolies and
site data’. For added safety you can also select the option below, which clears
your data when you close Chrome. Click Ok and close the Settings tab.
Simple ways to protect yourself
Add
Entry
- Limit the information you share
publicity. If you’re including your birthday in a social profile, avoid
stating your birth year – this is a key identifier, which trackers can use
to distinguish you from other people with the same name.
- Use a secondary email address when
registering for websites, forums, competitions or shopping online. Hotmail
and Yahoo offer free, quick to set up accounts.
- Use one browser for general web
activities and another for more sensitive information. Avoid suing ‘Like’
and ‘+1’ buttons.
- Regularly change your passwords and use a
separate one for each account. A password manager can be useful here.
- Make sure any browser you use has the
Privacy settings switched on. These are often off by default.
Super cookies
Cookies serve a useful purpose on most
sites, able to remember your user settings and preferences, but not all cookies
are good news. Flash, Super and Zombie cookies threaten our privacy and can
prove harder to eradicate.
“These types of cookies work by storing a
unique ID in multiple places at the same time,: explains AVG’s chief technology
officer Yuval Ben-Itzhak. “For example, if a user deletes a traditional cookie
in the browser but not in Flash, a tracking network could identify the user
through Flash and rewrite the original browser cookie with the same unique ID.
This makes the ID persistent and very effective in tracking users over a long
period. By simultaneously removing all types of cookies or other places where
unique IDs are stored, it is possible to minimize the chances of being
identifies and tracked.”
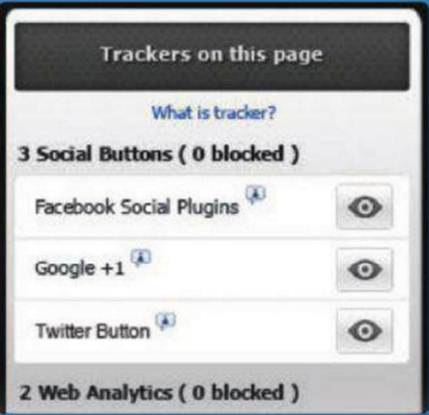
Trackers
on this page
The software company has also developed a
Do Not Track (DNT) feature for its Internet Security 2012 package, which is
compatible with Internet Explorer, Chrome and Firefox. DNT could provide more
effective protection than standard methods.
“The ‘passive’ DNT feature used in web
browsers works by providing a DNT header to the sites a user is visiting,” says
Ben-Itzhak. If this header is activated, the browser asks the site not to track
the user. The problem is that adhering to DNT isn’t compulsory.
Rather than hoping the website will not
track the user, AVG actively blocks the connection. Blocking third-party
cookies doesn’t guarantee users can’t be tracked; only by actively blocking the
tracking is the user fully in control.