With the revelation that the National Security Agency may
have been involved in everything from spying on U.S. residents to cracking
online encryption to collecting global financial data, computer privacy has
taken on all the cloak-and-dagger intrigue of a John le Carre novel.
We went right to the experts - the NSA itself - and pored
over the agency's security tips and recommendations (go.pcworld.com/ nsatips)
for its Department of Defense and intelligence-community customers. From there,
we identified seven simple measures that you can easily implement to protect
yourself from hackers and cybercriminals - and perhaps even from the NSA.

On its website,
the NSA offers extensive guidelines for securing computers.
Enable automatic software updates
Good security starts with the basics, of course, and nothing
is more basic than keeping your operating system current. So it's no surprise
that the NSA recommends enabling automatic updates in Windows.
Navigate to System and Security from the Windows Control Panel.Click
Turn automatic update on and off, and select Install updates automatically.
Encrypt your hard drive
The BitLocker encryption feature is built into the
Enterprise and Ultimate versions of Windows 7, as well as the Pro and
Enterprise versions of Windows 8. When enabled, BitLocker encrypts all of the
data on a storage volume, and it works in the background to protect the
contents of a Windows PC from unauthorized access.
BitLocker is an excellent first line of defense that takes a
few clicks to enable. However, if you're concerned that the full-disk
encryption technology may have been compromised by a backdoor deal with the NSA
(though there is no evidence of that so far), you can find alternative methods
(go.pcworld.com/nsaencrypt) to encrypt your data.

Encrypt your hard
drive
Tape over the webcam
Integrated webcams present excellent opportunities for
malicious hackers to spy on users. And although the webcam indicator light is
supposed to switch on when the camera activates, hackers have found ways to
disable the light in certain laptop models.
According to the NSA, a simple, low-tech solution is to tape
over your web cam - with black tape, naturally. If you're worried that the
tape's adhesive might damage the webcam, use tape to secure a small piece of
paper over the lens instead.
Disable the built-in microphone
Similar to the webcam, your laptop's built-in microphone -
typically enabled by default - can also fall prey to remote hijacking and allow
strangers and snoops to eavesdrop on your conversations.
To prevent that, launch the Sound applet from the Control
Panel. Click the Recording tab, select your laptop's microphone, and disable
it.
Of course, taking this step doesn't prevent a malicious
hacker who has already compromised your laptop from re-enabling the mic. If
you're really paranoid, you can disable the built-in microphone permanently by
poking it with the business end of a needle or paper clip. The espionage game
has its casualties.

Disable your
laptop's built-in microphone to ensure that your private conversations stay
private.
Disable unnecessary network services
Although it's impossible to lock out malicious hackers
completely, you don't have to make their task any easier. Start by disabling
network protocols and services you don't use. For small businesses, such
services likely include IPv6, Bluetooth wireless, or even Wi-Fi, if you use
deskbound laptops connected via Ethernet. And if you don't share file and
printer resources on your PC, disable sharing - a step that Microsoft recommends
(go.pcworld.com/disablesharing), as well.
Harden your account settings
Spend a few minutes tweaking your Windows account settings.
A good first step is to disable any guest accounts, to ensure that a password
is set for each account, and to disable automatic login.
Next, enable a screensaver and set it to start with an
inactivity timeout of between 1 and 5 minutes. To do so, right-click the
desktop, select Personalize, and then click Screen Saver. Select the On resume,
display Logon screen checkbox. Obviously, you will need to have a password
configured first for this step to work.
Lastly, require that users reenter their system password if
the PC has been inactive. Click Power Options in the Control Panel and select
Require a password on wakeup in the left column.
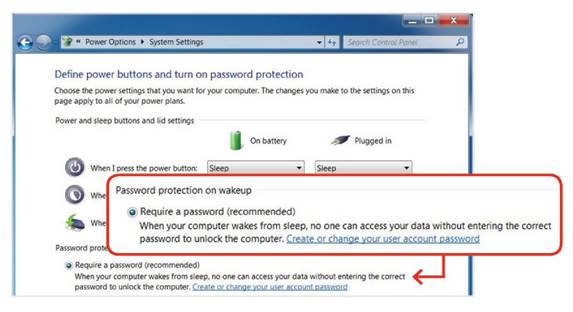
If you use sleep
mode, set the PC to require a password on waking up.
Don’t read email on an admin account
Web surfing on a user account with administrative rights is
kind of like walking through a bad neighborhood with your house keys in one
hand, your Social Security card in the other, and your ATM PIN written on your
forehead.
The usual advice is to avoid surfing the Web on an admin
account to limit the damage if a zero-day exploit compromises your account. Given
the growing number of attacks launched via email messages, it's a good idea to
extend this precaution to your inbox by reading email only on a non-administrator
account. This practice won't protect you from phishing attempts, though, so be
sure to stay on your guard against fake email messages, too.