Recognize & prepare for online threats
Malware, short for malicious software, is a
term used to cover all types of programs that attempt to gain
unauthorized access to your PC, steal information, and interrupt
computer operations. One of the best ways to avoid being tricked
by the different types of malware is to know what the software does
and how it’s likely to gain access to your computer. Here, we’ll examine
the most popular types of malware, and explain why you need multiple
security software tools in your anti-malware arsenal.
How does malware get in?
Whatever the type of malicious software, it
must first find a way into your computer. Many viruses and spyware are able to
find a way through by embedding themselves into Internet traffic, which is
smart: After all, Internet traffic typically appears legitimate to a firewall
(a device or software designed to detect illegitimate traffic). For example,
consider a virus that’s been attached to an email. Most firewalls are incapable
of examining the actual contents of an email, so the virus, with the email to
which it’s attached, would pass through your security unquestioned.

How
does malware get in?
Other ways of bypassing security via
Internet traffic include embedding malware in pop-up ads and Flash video
content, as well as taking advantage of existing vulnerabilities in your Web
browser and operating system. Continually installing updates for your operating
system and Web browser will help to ensure that any old security loopholes won’t
affect your computer. For instance, many hackers still use the Conficker worm,
which utilized a vulnerability in Windows to infect millions of computers in
2008, because some people refuse - or simply don’t know enough to - update
their PCs.
Viruses
These are designed to cause general chaos
on your computer. If you’re a victim of a virus, you’ll generally know right
away. Some common effects include corrupting files and the deletion of
important files that are required for Windows to operate. Before these types of
issues occur, it’s likely that a virus will attempt to try and take over your
PC so that it can download other viruses or use your computer to infect others.
For instance, a hacker may access your email client and send to all of your
friends and colleagues emails that include a link to a malicious file or
website.
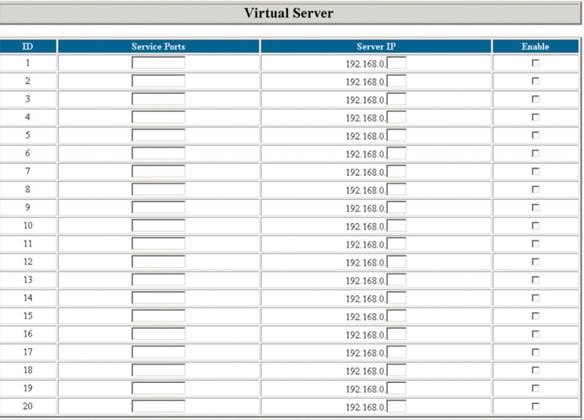
Routers
feature virtual ports that hackers will try to scan for vulnerabilities as a
way of getting into your system
One of the best ways to avoid viruses is by
using security software that offers multiple ways to detect viruses. For
example, some security programs use both signature-based databases and
heuristic types of detection, so the software can reference existing virus
rules and patterns to discover known viruses and variants, and block the file
or program from running before it has a chance to infect your computer.
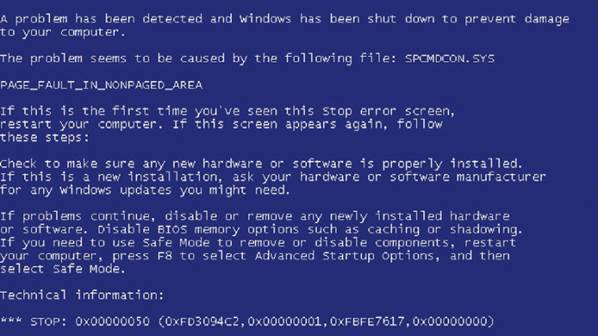
The
BSOD (Blue Screen Of Death) can be indicative of a hardware or compatibility
problem, but it can also be caused by a virus
Rootkits
A rootkit is a type of virus that allows
low-level access to your system while disabling your security software in order
to pave the way for a hacker (or another virus) to enter your system. A rootkit
can even attempt to prevent you from re-enabling your security software or
running security software that would detect and remove the rootkit and any
associated malware. A rootkit may even block any downloads on your PC, so that
you couldn’t even download another application to remove it. Thus, it can be
extremely difficult to remove a rootkit once it’s established a presence on
your PC. There are good anti-rootkit tools available (many of which are free),
and you may be able to remove the rootkit by using a different computer to
download the anti-rootkit tool and then running it on the infected machine.
Sometimes, though, the best way to remove the problem is to completely
reinstall Windows.
Spyware
Similar to a rootkit, spyware applications
hide themselves in your PC. But unlike a rootkit, spyware makes no obvious
changes to your PC. Instead, it’s designed to monitor your key-presses, the
websites you visit, and other activities to collect the data necessary to break
into your personal, financial, and work accounts. Once the information has been
gathered, it’s sent from your PC to criminal who will either use the data to
access your accounts and attempt to steal your identity or who will sell the
information to someone else who intends to do so. The best way to stop spyware
is by using security software with an anti-spyware component. Typically,
anti-spyware will actively block spyware from installing itself and will also
scan for and remove any existing spyware.
Spam
We’ve all come to expect a bit of spam in
our email accounts, and it’s important that we learn to avoid suspect messages,
because the email may be infected with malware. Perhaps the most dangerous
types of spam are phishing emails: messages that pretend to be from an
official, known, or trustworthy sender. The usual goal of a phishing attack is
to try and trick you into sending personal information, such as usernames,
passwords, and credit card numbers. (Or to click on a link that then takes you
to a site that requests this information). Security software with an anti-spam
utility is the easiest way to avoid dangerous spam, because it will filter the
messages from your email client.
A sweet suite
Although you can download or buy individual
applications that will guard against all of the malware we’ve covered here,
it’s generally easier and safer if you invest in a security suite that covers
everything you need to protect the computers on your network.
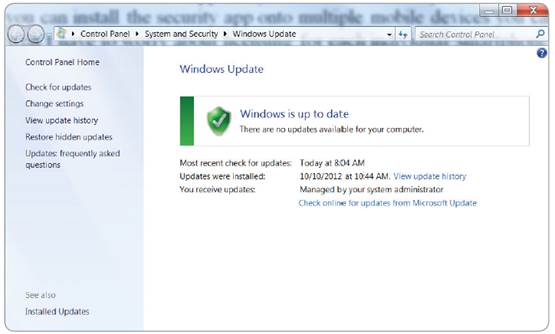
You
should also ensure that Windows itself is current, to help avoid any
vulnerabilities that hackers may have previously discovered
Malware Terminology
·
Virus:
A program designed to interrupt your
ability to use the PC, whether via a crash, lost files, or a corrupted Web
browser.
·
Spyware:
Monitors what you do and type on your
computer in order to gather data that will let hackers break into your
accounts.
·
Rootkit:
This malware shuts down your computer’s
security software and tries to block you from changing any settings or fixing
the problems it causes.
·
Spam:
Unasked-for emails, some of which may link
you to malicious, infected content.
Protect your tablet & smartphone
With an active connection to the Internet,
tablets and smartphones are also vulnerable to malware. For example, malicious
versions of Super Mario Bros and Grand Theft Auto recently got past Google’s
Play Store and were downloaded by up to 100,000 people. The rise in the
availability of mobile devices also makes them a target for cybercriminals. In
recognition of this shift, many security suites now come with a smartphone or
tablet app, in addition to desktop applications. With many such programs,
you’re allowed to install the security app onto multiple mobile devices, so you
won’t have to worry about licensing for each individual smartphone or tablet.
Keep
your Web browser up-to-date, so that old, already-resolved security issues
don’t leave you at risk