Are your apps spying on you? Does
Google mine your data? Are viruses and malware really a problem? We examine
whether your Android device should be a serious cause for concern...
Your Android phone or tablet is a mini it
makes calls, it lets you send email browse the web, write articles and p
movies. Whatever you can do on a desktop it is likely that you will be able to
do it on An But there is something else to think about data which you place on
your phone is likely value to someone else. Details of your con' email
addresses, passwords and social MS are just a small snapshot of the items which
would love to have. And with payment systems set to become standard, there Is
money at stake too.

For this reason security should be rather
high on the agenda. You want a situation where, should your Android device be
stolen, the Information is locked down and can’t be access. You want to be able
to pinpoint exactly where your phone is If It is stolen and you want to make
regular backups so that, if the device dies on you, the data doesn’t go with
it. You then want to ensure those backups are secure.
Malware: myth or menace?
There are other ways your device can be
compromised. It can be hit by a virus, malware or spyware. There are also
worries that the cloud services you trust with your data can be hit by hackers.
Reports In the newspapers suggest your apps are spying on you, that Google is
evil and is accessing your data and that payment systems such as Near Field
Communication are far from secure. This computer in your pocket suddenly seems
like a dangerous proposition.
“The Android platform Is consistently cited
as having the largest slice of the smartphone market pie, so it’s no surprise that
It’s become a favourite target for malware authors,” says Raj Samani, CTO of
security experts McAfee. “Almost all new mobile malware detected in the second
quarter of 2012 by McAfee Labs was directed at the Android platform, comprising
of SMS-sending malware, mobile botnets, spyware and destructive Trojans.”
Indeed, the number of malware samples
detected rose by 1.5 million from the first three months of 2012 to the second
quarter. A number of new threats also appeared including so called ‘drive by
downloads’, the use of Twitter for control of mobile botnets, and the
appearance of mobile ‘ransomware’. The number of malware samples being detected
is 100,000 a day.
It seems as though Android phones are
actually more at risk of malware than Apple’s iOS. This is due to the Android
system’s open nature. It is easier to create an app for Android and there is no
verification system before that app reaches the hands of users. Where Apple
vets each app ahead of its appearance on the App Store, there is no such process
for Android and so rogue apps can sneak through.
Of the new threats to be worried about, Ransomware
is one of the most devastating. Popular among a new breed of cyber criminals,
damage can range from a loss of photos and personal files to data encryption
and demands for money from large enterprises.
Botnets are also a viable threat, infecting
devices with malicious software and using it to generate spam, send viruses or
cause web servers to fall.
Social network Twitter is being used for
mobile botnet command and control. As such, the attacker can tweet commands
with relative anonymity and all infected devices will follow them.
“Users are Increasingly relying on their
smartphones for day to day activities,” adds Samani. “In turn, the sheer amount
of sensitive data being stored on unprotected devices presents a feast for
hungry cyber criminals waiting to steal your personal data.”
Do you need antivirus?
Unsurprisingly, perhaps, given that he
heads up a company which makes antivirus packages, Samani advises having the
necessary security installed on your Android smartphone will prevent that information
from falling into or being snatched by the wrong hands. There are certainly
lots of antivirus apps for Android which suggests there is an issue (contrast
that with iOS, for example). But just how necessary is it?
“Mobile security software can not only
prevent against viruses, but can provide features such as call and SMS
filtering, protection against malicious apps, and remote device tracking, lock
and wipe should your phone get lost or stolen,” says Samani. “Cyber criminals
are underhand and will look for any way to access the data on a device.”
The risk of infection, however, can be
minimised with both a combination of taking care and not opening up your device
to potential problems. Although Jonathan
Krause, the founder of Forensic Control,
pointed out to us that the Android operating system isn’t as tightly locked
down as it is on IOS or Blackberry phones, those who root their Android devices
are at most risk. “Not only are you likely to have voided your warranty, you’ve
also made the device more vulnerable to malicious software," he says. “In
this situation anti-malware software may help.”
Crucially, however, he says that most users
need not be too concerned. “There are steps you can take to minimise the
risks,” he adds. “If you’re the type of person to use less well-known apps, you
simply need to check other people’s reviews before you install on your device.
Essentially, though, if you’re a regular Android user who has no interest in
‘getting under the skin' of their device and if you install mainstream apps
then you’ve little to worry about. Otherwise, I would consider getting some
decent anti-malware software installed.”
How to find your lost device
Losing your phone or having it stolen
is a pain. All your vital data, emails, images and contact details are at risk.
With the Lookout app you can discover exactly where your phone is and use it to
track down your device...
1. Set up Lookout

After downloading Lookout from Google Play
and installing, you will be taken through a series of steps to set up your
security, backup and Missing Device facilities. If you go Premium, you will get
remote lock and wipe facilities.
2. Go to lookout.com
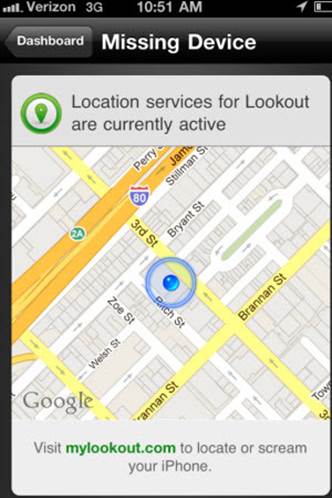
If your phone goes missing, go to
lookout.com on your PC or Mac. Clicking Locate under the Missing Device tab
pinpoints your phone using Google Maps, narrowing down until it finds the
street.
3. Send a scream

If you believe you have lost your phone,
send a scream to play a loud siren on your handset and make the J screen flash.
1 It would also I startle any I thief who m may have your phone.