Managing passwords with keychain access
In the innocent days of our computing
youth, many of us had to memorize just one password – the one we used to send
and retrieve our email over a glacially slow dial-up connection. User-account
passwords? For geeks. Shopping-site passwords? What shopping sites? iTunes
Store? App Store? Didn’t exist.
Make
Apple’s password management app your destination when you want to view, change,
or manage your passwords
It what may seem like a giant step
backward, we now juggle dozens of passwords. Fortunately, our Macs can store
those passwords and, in many cases, automatically fill them in when needed. But
there’s more to know about passwords and the Mac’s ability to store them.
Here’s a quick guide to what you can and can’t do with OS X’s passwords.
Keychains are key
Ever since Mac OS 8.6, the Mac has managed
passwords with Keychain, Apple’s password-management system. The Keychain
Access application (/Applications/Utilities) is the front-end to that system.
It stores a wide range of items including passwords for email, websites,
servers, network shares, Wi-Fi networks, and encrypted disk images. Whenever
you save a password, it’s stored in the Mac’s keychain.
The Mac places it various keychain files in
multiple locations: /System/Library/Keychains: /Library/Keychains; and youruserfolder/Library/Keychains.
Thankfully, the contents of these different keychain files are combined into
Keychain Access, so you needn’t worry about where they reside.
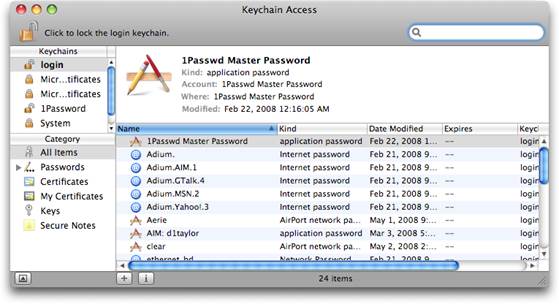
Launch Keychain Access, and you’ll see that
the window is divided into three panes. The top-left pane lists Keychains that
are accessible to you. Below that is the Category pane, where you can view
specific kinds of things stored in the keychain passwords, secure notes,
certificates associated with your account, encryption keys, and certificates
use broadly by your Mac. The largest pane, to the right, displays the contents
of selected category items – for example, all of the items that have a password
associated with them. Except in the case of certificates, you can double-click
on one of these items to open a window where you can view the item’s attributes
name, kind, associated account, location (a website or network address) – as
well as its access control (meaning the applications and services that
are allowed to access the item).
Recover passwords

Double-click
an item in Keychain Access, and you’ll get a window that shows it attributes
If you want to retrieve a forgotten
password, Keychain Access is the place to go. To learn the identity of a
password, select All Items or Passwords in the Category pane,
find the item that you want the password for, and double-click it.
In the resulting window, enable the Show
Password option. You’ll be prompted for the password for the login
keychain. Enter that and click Allow, and the password will appear in
the Password field.
Change the login Keychain’s password
Anyone
who knows your account’s password can access the items in this keychain and
then discover your other passwords
When you first set up a user account, the
account’s login password is also assigned to the login keychain, where new
passwords are stored by default. So you can simply enter the password you use
with your account to uncover a keychain item’s secrets.
If there’s a flaw in the Keychain Access
security setup, this is it. Anyone who knows your account’s password can access
the items in this keychain and then discover your other passwords. If you’re
concerned about that vulnerability, you can easily change the password for the
login keychain.
In Keychain Access, select the login
keychain and choose Edit ð Change Password For Keychain “login”.
You’ll be prompted to enter your current password (the one you now use for your
user account) and then enter and verify a new password. Do this, log out of
your account and then back in; when the Mac needs to use one of the passwords
stored in the login keychain, you’ll be prompted to enter it.
Autolock the Keychain
By default, once you’ve logged in, your
keychain will be unlocked, which isn’t terribly secure if others can access
your Mac when you’re not around. You can add a level of security that autolocks
your keychain. To do that, launch Keychain Access, select your login keychain,
and choose Edit ð Change Settings for Keychain login.
The sheet that appears shows two options:
‘Lock After X Minutes of Inactivity’ and ‘Lock When Sleeping’. If you choose
the first option and configure it to read something like 5 minutes, your
keychain will automatically lock if it hasn’t been accessed in the previous 5 minutes.
If an application needs access to your keychain after that time limit has
expired, you’ll be prompted for your login keychain password. If you enable the
Lock When Sleeping option, your keychain will lock when your Mac goes to
sleep. Click Save to implement the options you selected.
If you forget
If
you forget your login keychain’s password, you must delete the old keychain and
create a new one
You’ve changed the login keychain’s
password and forgotten the new password. Is there any hope? Regrettably, no.
Apple uses the Triple Digital Encryption Security standard, or 3DES, to secure
the keychain. You’ll just have to start over. Remove the old login keychain
from Keychain Access and create a new one: In the Finder, select Go ð Go to
Folder, and enter youruserfolder/Library/Keychains. A Keychains folder
containing your personal keychains will open. Find the login.keychain file, and
drag it to a safe place on your Mac.
Now launch Keychain Access and select the
login item that appears in the Keychains pane. It appears as an empty box,
indicating that it’s missing from the Keychains folder. Choose File ð New
Keychain “login”. In the resulting sheet, click Delete References.
Now chose File ð New
Keychain. In the resulting Save dialog box, name the new keychain login and
save it to the default location (your account’s Keychains folder). You’ll be
prompted to create and verify a password for this keychain. The passwords that
you add will now appear in this keychain. And yes, you’ll have to reenter
passwords stored in the old keychain when prompted.
Share your login Keychain
If you have multiple Macs, you may find it
convenient for each computer to have access to the same keychain. Here’s how to
do it: First, make a copy of the login.keychain file inside the Keychains
folder on the Mac that has the most complete set of passwords, and copy it to
your other Macs. Remove the login.keychain file from each Mac’s Keychains
folder and put it in a safe place in case something goes wrong. Place the
copied login keychain file in the user’s Keychains folder. Log out and then log
back in. if the login password on the Mac you’re currently using is different
from the one on this master Mac, you’ll receive a prompt asking you to provide
the login keychain’s password. Once you enter it, you should have access to the
same passwords as that master Mac.