How to make security questions
When you create a password, you might
choose to store it in a password manager, write it down, or commit it to
memory. Sometimes, however, things go wrong: You find yourself without access
to your password manager, you lose the paper on which you recorded you
passwords, you forget a password you thought you had memorized, or you remember
it wrong too many times and get locked out of the account.

When
you create a password, you might choose to store it in a password manager,
write it down, or commit it to memory
In such cases, online services need a
secondary way of granting you access to your account or your data. Sometimes,
the provider lets you click a link to have your existing password, a new
password, or password-reset instructions sent to the email address you have on
file. But if those mechanisms seem too insecure, the site may ask you to
respond to some verification questions for which you’ve previously provided the
answers.
Unfortunately, password-reset messages and
verification questions come with their own problems and risks. You can reduce
your chances of being hacked or of being unable to respond correctly to one of
these questions by following a few simple tips.
Prevent password-reset mischief

Take
extra care with your email account password
Of all your passwords, the one for your
email account may be the most valuable. That’s because whoever has access to
your email account can read and click links included in any password-reset
messages you receive (such as when you click an ‘I Forgot My Password’ link). A
hacker who has guessed or stolen just that one password can unlock many of your
other accounts and do all sorts of damage. You can limit your risk here in a
couple of ways.
Set up a dedicated password-reset account
Consider setting up a new email account for yourself (using a free service such
as Gmail) with an address that you’ll never share or post publicly. Use this
account only when you’re prompted to supply an email address for the purpose of
verifying or resetting a password. That way, even if someone breaks into your
main email account, your other accounts won’t be compromised.
Take extra care with your email account
password Choose an especially secure password for your email account. Make sure
to set your email client to communicate securely with the mail server – using
Secure Sockets Layer (SSL) protocols for example – so that your password never
travels over the air unencrypted. In Apple’s Mail, select Mail ð Preferences,
click Accounts, choose an email account from the list, and click Advanced.
There you’ll see the option Use SSL.
Question the questions
Security questions are supposed to have
answers that you’ll remember but that most other people won’t be able to guess.
Unfortunately, most of the questions you’ll see aren’t secure at all.
Your mother’s maiden name, for example, is
a matter of public record; and if you ever wrote a Facebook post about your
first pet, that is in the public domain, too. Some questions could have
multiple answers. Where did you meet your spouse? That might be in New York or
at Yankee Stadium.
Security
questions are supposed to have answers that you’ll remember but that most other
people won’t be able to guess
Devise memorable lies To address such
problems, lie. And don’t just lie, but come up with one or more answers that
follow the same rules as other passwords, to prevent guess-ability; use either
a reasonably long (but memorable) phrase or a series of random characters. So,
what was the name of my first pet? Why, it was bookends-qualitative. My mother’s
maiden name? Her dad was Mr. E27jrdU!8. It doesn’t matter what answers you
give, as long as you and only you know what they are.
One security expert says that he normally
uses the same pseudo-random answer everywhere, although some companies
(including Apple) require you to give different answers to each of several
questions meaning that you have even more password like data to keep track of.
Of course, you can write down your answers or store them in a password manager,
but then the same problems that stop you from accessing your password could
prevent you from accessing your security answers.

One
security expert says that he normally uses the same pseudo-random answer
everywhere
You might make up a little story for
yourself about fictional parents, cars, pets, and the like that you can then
draw on when asked for security answers on different sites.
Keep answers phone-friendly Remember that
you could wind up in a situation where you have to supply these answers over
the phone. Both you and the person on the other end will have an easier time
coping with a series of plain-English words than with a bunch of random
characters.
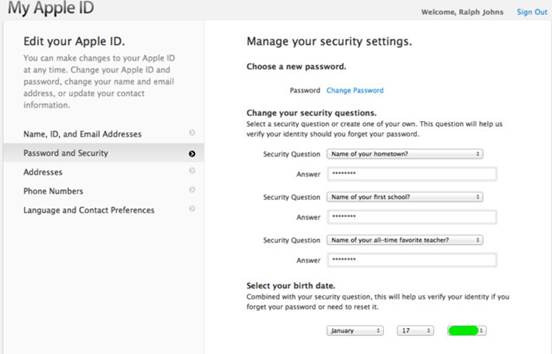
Update your Apple info To change the
questions or answers for an Apple ID (which you use for iCloud, for example),
go to the Apple ID page (appleid.apple.com), click Manage your Apple ID,
enter your username and password, and click Sign in. On the left, choose
Password and Security. Answer your existing security questions, and click Continue.
Then you can choose new questions and answers. Click Save.
Update your Google info If you have a
Google account, log in as you normally would. Click the gear icon located in
the upper-right corner of the window and choose Settings from the pop-up menu.
Click Accounts and Import, followed by Change password recovery
options. Under Security question, click Edit. Choose one of the
existing questions or write your own, and fill in your answer. If you also want
to change your secondary address, click the Edit link in the ‘Recovery
email address’ section and fill in the new address. Then click Save.