Scheduling Maintenance Tasks
When you manage desktop and laptop systems,
you'll often want to perform routine maintenance tasks on a periodic or
recurring basis. To do this, you can use the Task Scheduler service to
schedule one-time or recurring tasks to run automatically. You automate
tasks by running command-shell scripts, Windows Script Host (WSH)
scripts, or applications that execute the necessary commands for you.
Unlike earlier releases of Windows, Windows Vista includes an extensive
library of preconfigured tasks. These tasks handle everything from
uninstalling a Bluetooth device to defragmenting disks to performing
Windows Defender scans.
Understanding Task Scheduling
Windows Vista provides several tools for
scheduling tasks, including the Scheduled Task Wizard and the Schtasks
command-line tool. Both can be used for scheduling tasks on local and
remote systems. The Scheduled Task Wizard provides a point-and-click
interface to task assignment, and Schtasks is its command-line
counterpart.
Both
scheduling tools use the Task Scheduler service to monitor the system
clock and run tasks at specified times. The Task Scheduler service logs
on as the LocalSystem account by default. This account usually doesn't
have adequate permissions to perform administrative tasks. To overcome
this problem, each task can be set to run as a specific user, and you
set the user name and password to use when you create the task. Be sure
to use an account that has adequate user privileges and access rights
to run the tasks that you want to schedule.
| Note |
The focus of this section is on the Scheduled
Task Wizard. This is the primary tool you'll use to schedule tasks on
Windows Vista systems. To learn more about Schtasks, type schtasks /? at the command prompt or refer to Chapter 4, "Scheduling Tasks to Run Automatically," in the Microsoft Windows Command-Line Pocket Consultant (Microsoft Press, 2004).
|
Windows Vista has two general types of scheduled tasks:
-
Standard tasks Used to automate routine tasks and perform housekeeping. These tasks are visible to users and can be modified if necessary.
-
Hidden tasks Used to automate special system tasks.
These tasks are hidden from users by default and should not be modified
in most cases. Some hidden tasks are created and managed through a
related program, such as Windows Defender.
In Windows Vista, the creation and management of tasks
is much more sophisticated than ever before. Every task can be
configured to:
-
Run only when a user is logged on, or to run regardless of whether a user is logged on
-
Run with standard user privileges, or to run with the highest privileges required (including administrator privileges)
Because tasks created on Windows Vista are not
compatible with earlier releases of Windows, you cannot copy a Windows
Vista task to a computer running an earlier release of Windows and
expect the task to run. However, when creating the task, you can
specify that it should be created so that it is compatible with earlier
releases of Windows. This would then allow you to copy the task to
computers running earlier releases of Windows.
Tasks can have many properties associated with them, including:
-
Triggers Triggers specify the circumstances under
which a task begins and ends. You can begin a task based on a schedule,
user logon, computer startup, or processor idling. You can also begin a
task based on events, a user connecting or disconnecting from the
Terminal Server session, or a user locking or unlocking a workstation.
Tasks with event-based triggers can be the most powerful, because they
allow you to provide automated ways to handle errors and warnings.
-
Actions Actions define the action a task performs
when it is triggered. This allows a task to start programs, send e-mail
messages, and display messages.
-
Conditions Conditions help to qualify the
conditions under which a task is started or stopped once it has been
triggered. You can use conditions to wake the computer to run a task
and to start the computer only if a specific network connection is
available. You can use conditions to start, stop, and restart a task
based on the processor idle time. For example, you might want to start
a task only if the computer has been idle for at least 10 minutes, stop
the task if the computer is no longer idle, and then restart the task
again if the computer becomes idle once more. You can also use
conditions to specify a task should only start if the computer is on
alternating current (AC) power and stop if the computer switches to
battery power.
Viewing and Managing Tasks on Local and Remote Systems
The current tasks configured on a system are
accessible through the Task Scheduler node in Computer Management. You
can view and manage the scheduled tasks configured on a computer by
completing the following steps:
-
Open Computer Management. You are connected to
the local computer by default. If you want to view logs on a remote
computer, right-click the Computer Management entry in the console tree
(left pane) and then select Connect To Another Computer. Then, in the
Select Computer dialog box, enter the name of the computer that you
want to access and then click OK.
-
Expand the Task Scheduler node and then expand
the Task Scheduler Library node and related subnodes as necessary to
view the configured schedule tasks.
-
Select a task to view its properties using the tabs provided, as shown in Figure 1. If you want to manage the task, right-click the task and then:
-
q Delete a task by selecting Delete.
-
q Disable a task by clicking Disable.
-
q Edit the task's properties by clicking
Properties, making the appropriate changes in the Properties dialog
box, and then clicking OK.
-
q Export a task to a file that can be
imported on another computer by selecting Export. After you export the
task, use Computer Management to connect to the other computer,
right-click the Task Scheduler Library node, and then select Import
Task. You can then use the Open dialog box to locate and open the task
in the other computer.
-
q Run the task by clicking Run.
-
q If the task is running, stop it by clicking End.
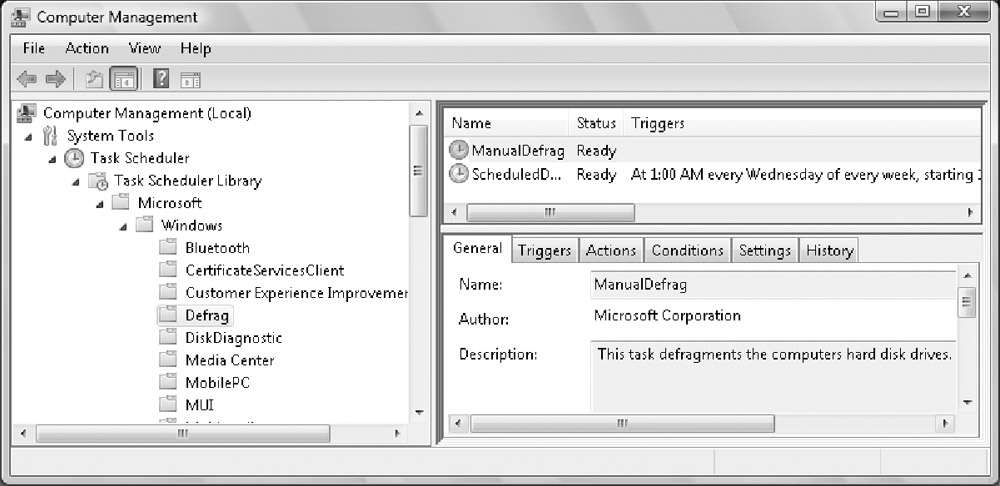
Figure 1: View and manage scheduled tasks.
| Note |
Although you can modify and delete user-created
tasks, most tasks created by the operating system cannot be configured
or deleted. You can view hidden tasks by clicking View and then
selecting Show Hidden Tasks.
|
You can view the scheduled tasks currently running on a computer by completing the following steps:
-
Open Computer Management. You are connected to
the local computer by default. If you want to view logs on a remote
computer, right-click the Computer Management entry in the console tree
(left pane) and then select Connect To Another Computer. In the Select
Computer dialog box, enter the name of the computer that you want to
access and then click OK.
-
Right-click the Task Scheduler node and then select Display All Running Tasks.
Creating Tasks with the Scheduled Task Wizard
To create a task using the Scheduled Task Wizard, follow these steps:
-
Open Computer Management. You are connected to
the local computer by default. If you want to view logs on a remote
computer, right-click the Computer Management entry in the console tree
(left pane) and then select Connect To Another Computer. In the Select
Computer dialog box, enter the name of the computer that you want to
access and then click OK.
-
Select and then right-click the Task Scheduler node and then select Create Task. This starts the Create Task Wizard.
-
On the General tab, type the name of the task and then set security options for running the task.
-
q
If the task should run under a user other than the current user, click
Change User Or Group. Use the Select Users Or Groups dialog box to
select the user or group under which the task should run and then
provide the appropriate credentials when prompted later.
-
q Set other run options as necessary
using the options provided. By default, tasks only run when a user is
logged on. If you want to run the task regardless of whether a user is
logged on, select Run Whether User Is Logged On Or Not. You can also
elect to run with highest privileges and configure the task for earlier
releases of Windows.
-
q On the Triggers tab, create and manage
triggers using the options provided. To create a trigger, click New,
use the options provided to configure the trigger, and then click OK.
-
q On the Actions tab, create and manage
actions using the options provided. To create an action, click New, use
the options provided to configure the action, and then click OK.
-
q On the Conditions tab, specify any limiting conditions for starting or stopping the task.
-
q On the Settings tab, choose any additional optional settings for the task.
-
q Click OK to create the task.
Troubleshooting Scheduled Tasks
When you configure tasks to run on a computer,
you can encounter several types of problems. Some tasks won't run when
they are supposed to. Others will start and won't stop. To determine
the status of a task, select the task in the Task Scheduler and note
the status, last run time, and last run result. If a task has a status
of Queued, it is waiting to run at a scheduled time. If a task has a
status of Ready, it is ready to run on its next run time. If a task
should be running automatically but has a Last Run Time of Never,
you'll need to check the task's properties to determine why it isn't
running. If the Last Run Result is an error, you'll need to resolve the
referenced problem so the task can run normally. Check a task's
properties by clicking its entry in the Task Scheduler. The History tab
provides detailed information on the task, from creation to its last
run time. Use the history information to help you resolve problems with
the task.
A task that is listed as Running might not in fact
be running but instead might be a hung process. You can check for hung
processes using Last Run Time, which tells you when the task was
started. If a task has been running for more than a day, there is
usually a problem. A script might be waiting for input, it might have
problems reading or writing files, or it might simply be a runaway task
that needs to be stopped. To stop the task, right-click it in the Task
Scheduler and then select End.
 


 
|