Protect your privacy, increase security and
access any web content without restrictions. Roland Waddilove shows the
benefits of a VPN
Picture the following two scenarios. The
first is someone that frequently travels abroad and while they’re away they
want to keep up with their favourite television shows. They can’t bear to miss
an episode of Eastenders. No problem, you think; they just need to log into
iPlayer at the BBC website and watch it over the internet. Sadly, though, it
won’t work because iPlayer can only be accessed from within the UK and no one
abroad can watch the streaming television shows. It doesn’t matter that you’re
a licence payer: if you’re abroad on holiday or business, then tough.
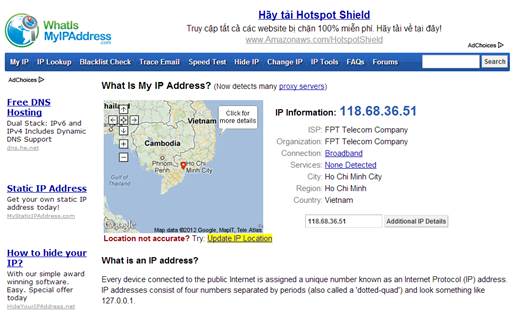
This
website works out where in the world you’re located. With a VPN it’s completely
wrong
The second scenario is someone that values
their privacy but also likes to use the internet. It is debatable whether
internet and privacy belong in the same sentence, because everywhere you go and
everything you do on the internet is tracked by someone somewhere. Advertisers
and websites spend a lot of time and effort gathering information about people visiting
websites and using web services. It’s also possible for someone not just to
track the things on the internet that you use, but also to eavesdrop on the
communications. They could intercept the network traffic and analyse it or even
change it, which is a scary thought.
What Is VPN?
The solution to both of these problems is a
VPN or virtual private network. The internet is a public network and computers
communicate by sending packets of data to each other through numerous wires,
cables, routers, switches and hubs. At any point the data can be intercepted
and read, at least in theory, and you can see where it came from and where it’s
going to. A VPN is a sort of private network that operates over the public
internet.
You
can’t watch iPlayer from abroad, even if you’re a licence payer
Basically, the data is encrypted before
being sent and it’s decrypted at the receiving computer. The encryption used
means that if anyone tries to read the data, they wouldn’t get very far at all,
not even with a million-pound supercomputer.
A VPN offers privacy and security over the
inherently public and insecure internet. Only the sending and receiving
computers using the virtual private network can read the information that is
being exchanged between them and it’s practically impossible for anyone to hack
into it. What’s more, it’s also impossible to tamper with the data and anything
that changed it would be immediately obvious. Of course, nothing is actually
impossible to hack, but if it takes a Titan Supercomputer (currently reckoned
to be the fastest in the world) to crack the security, then it’s pretty near
uncrackable and is certainly good enough for most people.
“A VPN offers privacy and security over the
inherently public and insecure internet”
So a virtual private network is between two
computers, which leads to the obvious question of how it’s set up and how it
takes place. What are the practical difficulties in setting up a VPN? The main
requirement is that both computers must be running VPN software. Large companies
have internal networks through which employees can exchange files, access
resources and send messages. If the company has two geographically separated
offices, they can be connected over the internet using a virtual private
network. Both offices can then use a single network, and employees in one
office can communicate with people in the other office like they were just down
the corridor in the same building. What’s more, an employee that’s on the road
or working from home could connect to the office network using a VPN and it
would be just the same as if they were in the building. Even though data is
being sent over the public internet, it’s completely private and separate from
the rest of the internet traffic.
Internet Censorship
In the Western world we take free speech
for granted and don’t give a second thought as to what we say and who hears us.
Everyone is entitled to their own opinion we say, even if we don’t agree.
However, in some parts of the world you can get into serious trouble for airing
your opinions in public and on the internet. In fact, you might not be allowed
to access certain websites and services. Blocks can be put in place that limit
what is available on the internet. Only recently, Iran blocked access to Google
search and email services. What’s more, authorities said they would prosecute
anyone who criticised government officials. There are dozens of other countries
that limit web content and free speech too.
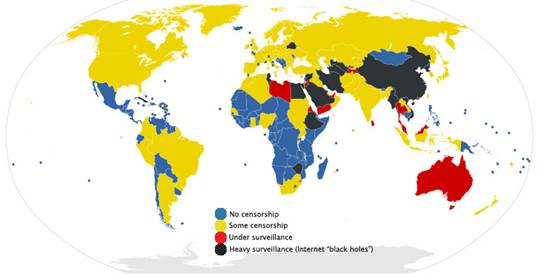
Internet
Censorship Map
With a VPN, though, no one knows what
you’re doing on the internet, which is great for paranoid people who dislike
the idea of people being able to snoop on them and watch their activities. It’s
possible to connect to a VPN service, which has an exit point (computer)
located elsewhere in the world. This allows them to access content or to air
their views on the internet, but as communications are encrypted between the
remote and local computer, the authorities cannot spy on them or block them.
You cannot connect to any old computer on
the internet, such as a website, using a VPN because web servers do not run VPN
software. What you can do, though, is to connect your computer to another
computer using a VPN and then that computer connects to the website in the
normal manner. The remote computer fetches the web page or whatever information
is requested, encrypts it and sends it back to your computer.