How to secure your tablet against attacks

Your
tablet is similar to your smartphone in a lot of ways, including its
susceptibility to attack
Its portable form factor makes it great for
plane rides, commutes, and all manner of travel, but those virtues also make it
an ideal target for Wi-Fi snoopers, thieves, and cybercriminals. But because we
use tablets differently than we use smartphones, they’re more susceptible to
certain kinds of attacks than smartphones. Read on to determine how best to
lock your tablet tight against threats.
Dedicated security apps
Similar to smartphones, tablets can take
advantage of security apps from the respective platform’s application store.
These range from simple RSS feeds of virus and malware alerts to more
sophisticated scanners that check the apps you’ve downloaded for spyware and
malware, built-in browsers that offer a more secure Web experience, and device
location services that help your find your device if it’s lost or stolen.
Because you tend to do more Web browsing on
a tablet than on a smartphone, you need to be more aware of potential Web-borne
threats. Visiting a malware- infected URL can compromise your identity. For
this reason, it’s a good idea to seek out software that includes a secure
browser. In lieu of that, a URL checker can provide real-time protection
against Web sites that are known to be malicious in nature.
Download with care
Like smartphones, tablets become more
useful as you download more apps. This reliance on third-party code for core
functionality can leave you vulnerable to apps, often free, that claim to be
something you’d really like to have, but which can end up stealing your data,
compromising your contacts, and worse.

You
take a risk every time you install an application from an unknown source
Thankfully, the first-party application
stores from which you download apps have strong vetting processes designed to
prevent the vast majority of malicious apps from becoming generally available.
Some of these sour apps do get through, though, so a little common sense when
downloading can help you stay safe. Avoid downloading free apps that sound too
good to be true, inspect the reviews for evidence of the app not performing its
advertised function, and read through the permissions with a critical eye
before you tap Install. There’s no reason, for instance, that a Sudoku app
needs access to your phone state and identity info.
The real risk here comes when downloading
apps from unknown sources. The simplest solution is to avoid this as much as
possible.
Audio video revolution
Thanks to tablets’ large and vivid screens,
we spend a lot of our time with them viewing videos. In your quest to see
something new, however, resist the lure of free movie streaming and download
sites. The denizens of the Web who have no qualms about violating copyrights
often have similarly little regard for the sanctity of your personal data. The
same can be said for music downloads and apps that purport to offer unlimited
music downloads for free.
You
love watching movies on your tablet, but paying for them is the safest way to
watch
Gone but not lost
If your tablet is ever lost or stolen,
you’re not only out the cost of the hardware, but you also have to worry about
any financial, email, and Web service accounts that may have been compromised.
One of the first things you should do is enable a password or pattern-based
lock screen on your device.

A
passcode or pattern unlock screen can keep your data safe if your tablet ever
falls into the wrong hands
Tablets on all platforms also offer apps
that let you look up the current location of your tablet on a map, play an
alert tone, and even remotely wipe the device. Some apps can even use the
tablet’s front-facing camera to take a snapshot of the potential thief and
email it to you.
Total tablet security
Tabbing safely starts with being cautious
with regard to your tendency to download apps, stream video, access Wi-Fi, and
browse the Web. Follow our advice and you’ll be significantly less likely to
run into trouble with your tablet.
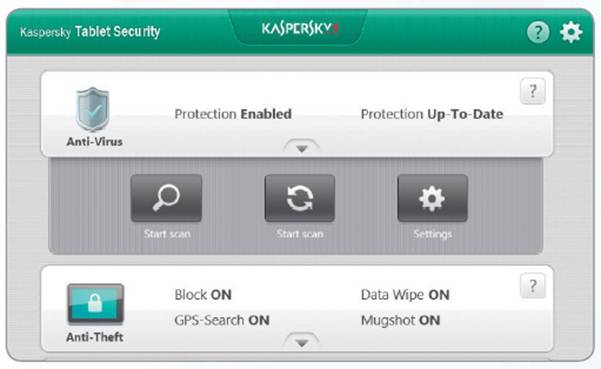
Apps
like this one can significantly improve your sense of security when using your
tablet