In the past couple of years, attacks on
Gawker.com and LinkedIn resulted in hackers gaining access to millions of
passwords. The incidents have heightened awareness for the importance of using
strong passwords, as these and other websites have advised users to change
their passwords to something different (at least) or something
difficult-to-guess and even potentially unique (even better). So you may be
wondering: What separates a good password from a bad one? And how, if you heed
the warnings about not using the same password for multiple web-sites, do you
keep track of all the passwords you create?

What
separates a good password from a bad one?
Best practices
A password shouldn’t be a simple word,
because hackers typically have software that can attempt up to thousands of
dictionary combinations. And because some websites require a number in the
password, the automatic hacking tools typically add a single digit behind the
common words and phrases. Thus, a password such as “home5” isn’t any more
secure than “home.” Other unwise choices include passwords that involve
personal information that a hacker or someone with personal knowledge of you
could have access to. For example, a last name, a partner’s first name, a
child’s name, or a number combination that involves the birthday of yourself or
a loved one is not advisable.
The
best password would be a random combination of uppercase and lowercase letters
and numbers
The best password would be a random
combination of uppercase and lowercase letters and numbers. The longer the
string, the harder the password will be to crack. The downside is that the
random assortment of characters isn’t easy to remember, so a long set of mixed
characters isn’t really practical. Fortunately, there are a few easy tips for
creating complex passwords that are memorable. One common method is to use the
first letters of a favorite phrase or lyric. For instance, “I pledge allegiance
to the flag of the United States of America, and to the Republic for which it
stands” could become Ipa2tFotUSAattRfwis. In this example, we mixed the
uppercase and lowercase letters by capitalizing the letter for Republic. The
key is that the phrase be easily remembered and that it fit within the
prescribed password size and requirements.
Why you shouldn’t repeat passwords
To
protect yourself, you could keep a list of your usernames and passwords in an
encrypted file on your PC or smartphone
Another issue that often comes to light
following major website attacks is that many users choose to use the identical
password for multiple sites. We know that it’s tough to remember all the
different passwords, or even which passwords correlate with a given Web
service. And storing the passwords somewhere whether on a sticky note or a
spreadsheet on your PC isn’t advisable because anyone who has access to your
computer could also make off with your passwords.
To protect yourself, you could keep a list
of your usernames and passwords in an encrypted file on your PC or smartphone.
However, if your computer crashes or you lose your phone, you risk losing that
list. In which case, your only remedy would be to contact an administrator of
each Web service to retrieve your passwords. Some people have turned to
password manager tools to keep track of their many usernames and passwords for
sites.
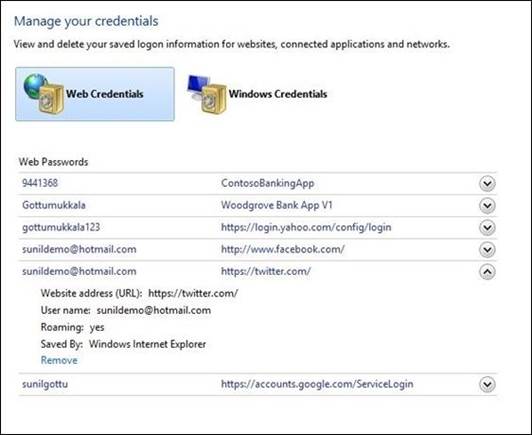
Password managers
When using a password manager, you only
have one master password to remember, and it becomes your key to unlocking the
credential storing software. Password manager utilities are available in
standalone (offline) and Web utility (online) options. Although password
manager features vary, the programs typically work the same. You need to first
create an account, which you secure behind a master password, and then you save
all your usernames and passwords into the program. The software encrypts your
data, so only individuals with the master password can access the files.

When
using a password manager, you only have one master password to remember, and it
becomes your key to unlocking the credential storing software
After you add a username and password for a
specific website, the manager program will automatically enter your secure
login information when you access that site. Not only does this method reduce
the burden of remembering the credentials, but it also is a deterrent to
hackers who may use key-loggers to monitor the keys you press in the hopes of
gaining knowledge about your usernames and passwords.
Password manager programs are also
beneficial because the one-click logon will save you time when logging in to
websites. Another plus is that many of these programs support a variety of
popular Web browsers, including Microsoft Internet Explorer, Mozilla Firefox,
and Google Chrome.
Key password manager features
Some
password managers feature random password generators that are ideal for
creating highly secure passwords
Some password managers feature random
password generators that are ideal for creating highly secure passwords. Once
the program generates a password, it saves the password and links it to the
website and username you prefer so you never need to remember the complex
sequence. Another popular feature is automatic form ill, where the password
manager enters your saved personal information (such as name, address, phone
number, or credit card number) into Web forms. Similar to the automatic
password fill-in, automatic form fill can deter key-loggers from stealing your
personal identity.
You can also download password management
apps for your mobile devices. Some apps work in conjunction with an online
service, but in general such apps will at least provide a PIN- or
password-protected space on your smartphone or tablet for securely storing
passwords and other vital information.
The cons of password managers
Because you probably won’t be physically
typing in passwords very often, it’s much easier to forget your usernames and
passwords. And if you need to get into your accounts from several computers, it
may take extra time to do so through an online password manager utility. You
may also run into issues if you use an offline password manager and need to
access your passwords on a different PC, such as one at a hotel or at work.