Norton Internet Security
Symantec’s 2013 edition of Norton Internet
Security ($73.5 for one year and three PCs) is a solid performer with a
polished, touch-optimized user interface. This security suite didn’t totally
dominate its competitors, but it did completely block, detect and disable all
malware in our rear-world tests, and it performed well enough overall to snag
second place in our round-up.
Symantec’s
2013 edition of Norton Internet Security
Norton’s excellent showing in our
real-world attack test indicates that it should be effective at blocking
brand-new malware attacks as it encounters them in the wild. As noted in the
F-Secure review, of the security suites we tested, four others were also successful
at completely blocking 100 percent of attacks: Bitdefender, F-Secure, G Data
and Trend Micro.
Norton produced stellar although not
perfect results in detecting known malware. In our malware-detection test, it
successfully detected 99.8 percent of known malware samples. Norton also put up
a perfect score in our false-positive test: it didn’t mistakenly identify any
safe files, out of more than 250,000, as malicious.
Norton does and acceptable job of cleaning
up a system that has been infected, but it missed some infections in our
evaluation. It detected and disabled 90 percent of infections, and cleaned up
60 percent of infections. This is a decent, but not fantastic showing – seven
of our tested suites detected and disabled 100 percent of infections, and six
cleaned up all traces of infection at least 70 percent of the time.
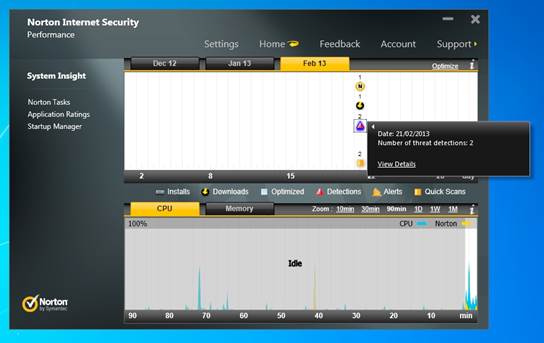
The
package required just 1 min, 19 secs to complete an on-demand scan, and 2 mins,
55 secs to complete an on-access scan – both time represent better-than-average
results
On the other hand, Norton is a relatively
lightweight program that won’t bog down your system. It added about half a
second to startup time (compared to a PC that had no antivirus program
installed), and also added three seconds to shut down time; in all our other
speed tests, it was faster than average when it comes to scanning speeds, as
well. The package required just 1 min, 19 secs to complete an on-demand scan,
and 2 mins, 55 secs to complete an on-access scan – both time represent
better-than-average results.
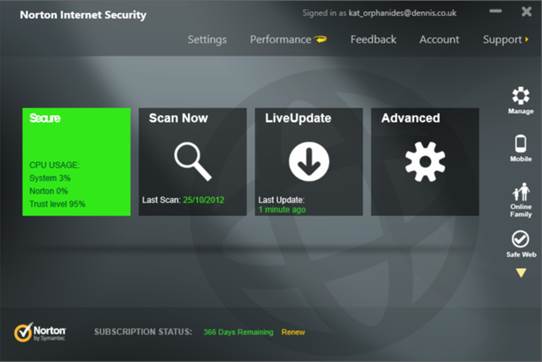
Norton’s interface is very polished and
simple, and the program installs with just one click. The main window has
tile-like buttons, which look designed to work well with Windows 8 touch
systems. You’ll find four tiles on the main screen: a tile that shows your
protection status, along with information about your CPU usage; a ‘Scan Now’
tile; a LiveUpdate tile (which you’d use to install any updates to the suite);
and a tile for advanced settings. You can also access the settings via the
Settings tab.
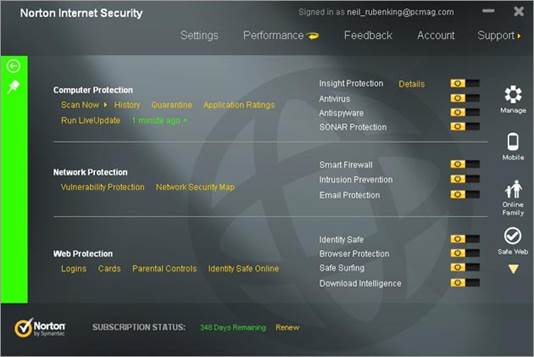
The Settings menu is relatively easy to
navigate, although it has more options than a beginner will need. Still, Norton
does a good job of explaining different features and toggles, and a help button
(which takes you to Norton’s online support site) is always located next to
confusing terms.
The
2013 version of Norton Internet Security is a good one, especially if you’re a
Windows 8 user
The 2013 version of Norton Internet
Security is a good one, especially if you’re a Windows 8 user.
Trend Micro Titanium Internet Security
2013
Trend Micro Titanium Internet Security 2013
($89 for one year and three PCs) certainly lives up to its name. This
‘titanium’ security suite didn’t let anything get through in our tests. It
earned excellent marks in just about every category. It also has a
user-friendly interface and a quick installation process.
In our real-world attack tests, which
indicate how well an antivirus program will be able to block new malware
attacks as it encounters them in the wild, Trend Micro completely blocked every
threat it faced. This means the program should be able to keep you very secure,
even when new malware is introduced in the future.
Trend
Micro Titanium Internet Security 2013
Trend Micro nabbed high marks in most of
our other security tests, which exposes the program to a collection of malware
that had been introduced in the preceding four months, Trend Micro’s package
detected 100 percent of known malware samples. In our false-positive which
checks to see whether a product mistakenly flags a known safe file as being
dangerous, it identified just one safe file (out of over 250,000) as malicious.
The suite also did very well in our cleanup
test: it detected and disabled 100 percent of infections, and it managed to
fully purge the system of 80 percent of those infections. This result puts it
in second place, tied with G Data and Kaspersky, for total cleanup rate.
Trend Micro Titanium Internet Security 2013
is also a speedy and lightweight program – most of the time. In our performance
tests, the program added just 0.3 seconds to startup time (compared to a system
that had no antivirus program installed), and three seconds to shut down time.
However, we found that it dragged down file-copy operations more than most of
its competition.
The suite’s scan times were on the slow
side, too, with an on-demand (manual scan taking 1 min, 50 secs (as compared to
the average time of 1 min, 33 secs), and an on-access scab requiring 5 mins, 41
secs (as compared to the average 4 mins, 50 secs).
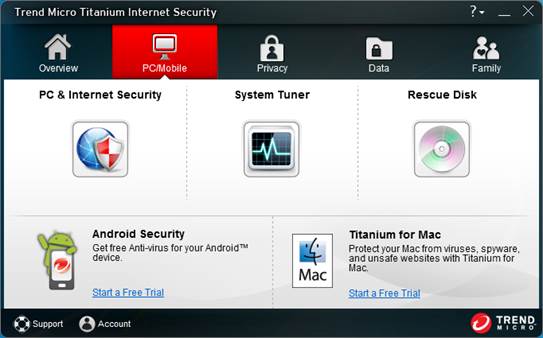
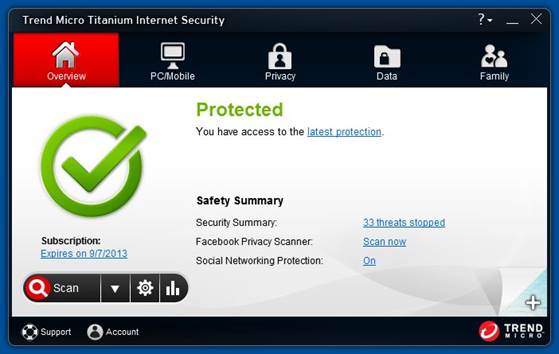
The
main window has five tabs along the top: an Overview tab, and others for
PC/Mobile, Privacy, Data and Family
Installing the Trend Micro package is a
breeze – you have just three screens to click through and an optional
registrations screen (which asks only for your email address). Note, however,
that the program does try to install three separate Firefox add-ons; a browser
exploit prevention add-on, which blocks malicious code from running; a
certificate add-on, which checks the safety of websites, links and wireless
network connections; and a toolbar add-on.
Trend Micro’s user interface is relatively
easy to understand, although it’s not as polished or attractive as AVG,
F-Secure or Norton’s. The main window has five tabs along the top: an Overview
tab, and others for PC/Mobile, Privacy, Data and Family. The Overview tab shows
your protection status, along with some additional stats (such as how many
threats have been stopped). This screen also has a scan button, a settings
button and a security-report button.
The PC/Mobile tab shows PC- and
mobile-related security features, such as the system tuner and the rescue-disk
creator, as well as links to get Trend Micro’s apps for your Android devices
and Mac systems. The Privacy tab deals with social networking, the Data tab
covers data security along with Trend Micor’s secure erase feature, and the
Family tab holds parental controls.
This
security suite has excellent performance, a quick installation process, a
user-friendly interface and speedy scans
The settings pane, which you can access via
the first tab, features basic settings for virus and spyware controls, internet
and email controls, and exception lists. You’ll also find a button for other
settings, such as system startup, network settings, and the background picture
for your main window. Trend Micro’s settings don’t seem to be overly geared
toward the advanced user, but the suite could still of a better job of
explaining the settings and features found within the program.
Overall, Trend Micro Titanium Internet
Security is a great choice. This security suite has excellent performance, a
quick installation process, a user-friendly interface and speedy scans. Its
settings pane is a tad confusing, but that’s a minor issue considering the
protection you’ll be getting.