We tested security suites on PCs,
tablets and smartphones to evaluate how well they protect against viruses and
other threats
If you’re like a lot of people, when it
comes time to renew your security software, you may ask yourself, “Do I really
need to upgrade to the latest version?” Keeping up-to-date is generally a good
idea, though, since new threats surface constantly. And if you value mobile
security or use a social-networking site, this year’s crop of security suites
is worth paying attention to.
An increasing number of security suites now
feature special tools to help protect you on social networks – a growing target
for spammers, scammers and other parties who want to get at your personal
information. For example, Trend Micro’s Titanium Internet Security suite comes
with a handy tool that highlights any possible areas of concern involving your
Facebook privacy settings. Various suites also include tools that will scan
links so that you aren’t duped into clicking a malicious link hidden behind a
URL shortener.

If
you’re like a lot of people, when it comes time to renew your security
software, you may ask yourself, “Do I really need to upgrade to the latest
version?”
If you own a smartphone or tablet, or both,
the security class of 2013 has some new tools of you. And some security
packages come with a mobile app that provides protection against mobile malware
or includes other features such as GPS tracking to help you find your phone
should it go missing. These apps often also include remote-wipe capabilities
that let you delete the contents of a missing phone or tablet so your private
data doesn’t end up falling into the wrong hands.
In addition, Windows 8 has changed the way
security software makers design their programs. Many of the suites we looked at
this year have redesigned interfaces that include larger buttons and controls
in an effort to be more touch-friendly.
We teamed up with AV-Test, a respected
antivirus testing lab based in Germany. AV-Test, ran each suite through
comprehensive battery of tests to find out how well each would stand up to the
worst malware currently in existence. AV-Test also performed speed testing to determine
whether the suites will slow your PC to a crawl. We analyzed the data that
AV-Test provided. And then tried each of the products to help you decide which
suite to go for. We explain our testing methodology at tinyrl.com/at26vzr.
Note: beside the top five suites discussed,
here, we tested four others that ranked a cut below. These are, in order,
McAfee Internet Security 2013, G Data Internet Security 2013, AVG Internet
Security 2013, and Avira Internet Security 2013.
F-Secure Internet Security 2013
F-Secure Internet Security 2013 ($58.5 for
one year and three PCs) came in first in several of our malware-detection,
-blocking and removal tests. It successfully blocked attacks, detected and
disabled infections, and proved adept at cleaning up all traces of malware.
In our real-world attach test, F-Secure
completely blocked 100 percent of attacks. This test indicates how well the
product might successfully block new malware attacks as it encounters them in
the wild. But F-Secure wasn’t unique: of the nine security suites we tested,
four others also managed to completely block all attacks: Bitdefender, G Data,
Norton and Trend Micro.
F-Secure
Internet Security 2013
F-Secure also put up great scores in our
malware-zoo detection test: the suite detected 99 percent of known malware
samples. This score puts it in the top five of the security suites we tested,
although it’s at the bottom of that group (G Data, McAfee, Norton and Trend
Micro all posted detection rates of 99.7 percent or higher). F-Secure flagged just
two safe files (out of more than 250,000) as malicious, which is a good
false-positive rate overall. However, since four of the suites achieved a
perfect score in false-positive testing, and two suites flagged only one safe
file as malicious, on this measure F-Secure still ends up in the bottom half of
the list.
In our system cleanup test, F-Secure
performed very well. In fact, it’s at the top of the list (alongside Bit defender)
after detecting and disabling all infections of our test computer and completely
removing 90 percent of infections. So F-Secure should effectively dispatch any
malware it finds on your machine.
While F-Secure does an excellent job of
detecting, disabling, blocking and cleaning up malware, all this power comes at
a price: F-Secure added six seconds to our startup time (compared to a system
with no antivirus software installed) – the worst showing of all the suites we
tested. It also added five seconds to shut down time. F-Secure performed well
in the rest of our PC speed tests overall, but it significantly slowed
application installation.
Scanning
speeds were much better, though
Scanning speeds were much better, though.
F-Secure took second place in both on-demand (manual) scan tests (1 minute, 16
seconds) and on-access (automatic) scans (3 mins, 50 secs). Both results are by
a healthy margin better than average.
The suite installs quickly and easily, with
just four screens to click through and no restart required. It doesn’t install
any extras (such as a toolbar), nor does it change any of your default
settings. It does install a launcher, which is what you open when you
double-click the program’s system tray icon. The launcher has three buttons to
take you to different program screens: a computer-security screen, an
online-safety screen, and a third for F-Secure’s website.
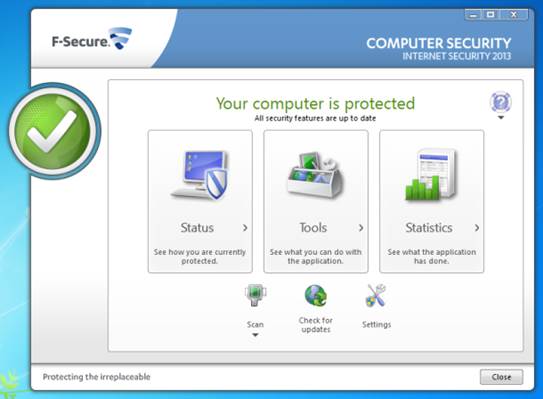
F-Secure’s user interface is sleek and easy
to understand. It presents a large round checkmark (or X mark) that shows your
protection status, as well as three modules for checking your security status,
F-Secure’s extra tools and features, and statistics and reports. Below these
modules is a scan button, and update button and a settings button. The settings
are fairly easy to get around, and each screen has a quick explanation of what
the feature does and how it works.
This
security package adds a little extra weight to your system but, if you can get
past those performance issues, it’s a great program
With excellent protection and a very
user-friendly interface, F-Secure is definitely worth your cash. This security
package adds a little extra weight to your system but, if you can get past
those performance issues, it’s a great program.