Protect your Windows installation
from dubious software. We show you how to test downloads in a protective
sandbox
If you never used the internet there would
be little need for security software but life without the web would be
unthinkable. The internet can be extremely useful for a wide range of
activities, from social networking with friends to collaborating on work
projects with colleagues.
Viruses, Trojans, spyware and other malware
can find their way on to your PC through various mechanisms. They can be
automatically downloaded when you visit a dodgy site, or you might be tricked
into running them via an email attachment or on the back of a legitimate
program.
It’s important to install and keep up to
date both an antivirus and an anti-spyware program, but these alone are not
infallible. You can boost your PC’s defences with a sandbox. In the same way
that children might play in a physical sandbox out of harm’s way, you can set
up a virtual sandbox as a safe place in which to browse the web and run
software.
You might think you know what’s safe and
what’s not, but it’s easy to get caught out. And if less tech-savvy members of
the family are also using the PC, a sandbox can be a useful safeguard.
Any software running within a sandbox is
unable to access your Windows installation. It won’t be able to change
settings, mess with files, attack your web browser or play out any other of its
malicious intentions.
A sandbox makes the web a much safer place,
whether you’re using it to conduct web chats, for online banking or, as we
outline here, testing software. Having tested your download in the sandbox,
you’ll know whether it’s safe to install It on your hard drive. You can also
open email attachments in safety.
Several free sandbox utilities are
available, such as BufferZone Pro and Sandboxie. In the following tutorial
we’ll show you how to use BufferZone Pro. You can download and run software,
open email attachments, browse the web, chat and more in a safe zone. You can
even access USB devices.
Setup a sandbox
Step 1

Head to trustware.com and download
BufferZone Pro. Open your PC’s Downloads folder and double-click
BufferZoneProFree.msi to install the software. Click through the pop-ups, then
restart Windows.
Step 2
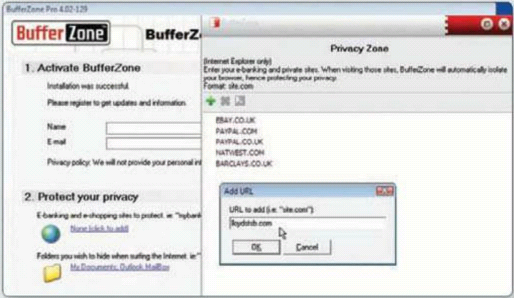
BufferZone Pro starts up with Windows;
enter your name and email to activate it. To configure certain sites to always
run in the sandbox, click ‘None (click to add)’ under ‘Protect your privacy’.
Click the + button and enter the URLs of shopping and banking sites.
Step 3
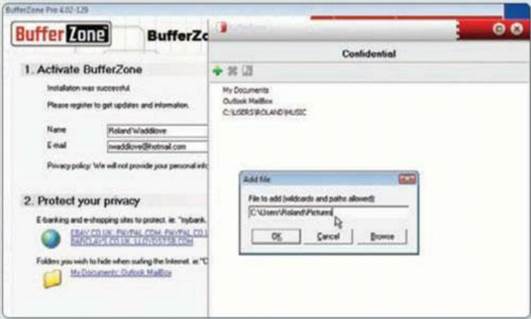
It’s also possible to hide folders on your
PC while you’re browsing the web. BufferZone hides My Documents and the Outlook
Mailbox by default; to add more, click the + button and type in the path to the
folder you wish to hide.
Step 4
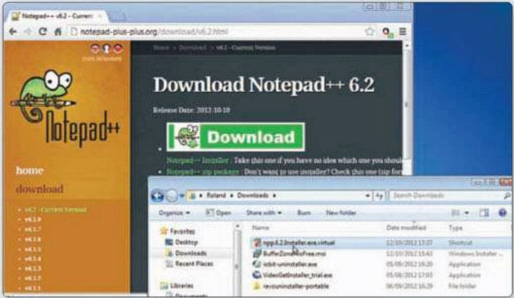
Click Finish and BufferZone will open a web
browser. You can now browse the web and download software. We downloaded
Notepad++ 6.2, but any site or software will do. Open the Downloads folder and
notice that the setup file has a .virtual file extension.
Step 5
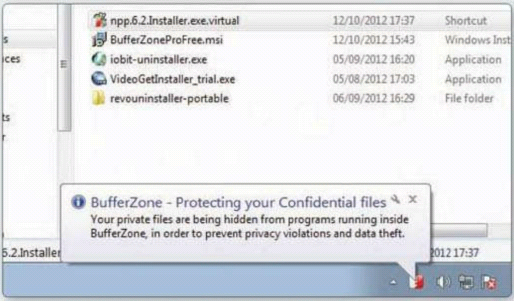
Double-click the setup file to install your
program. It will look like any other software installation, but notice the
BufferZone messages in the bottom-right corner. BufferZone is protecting the
computer during the installation.
Step 6
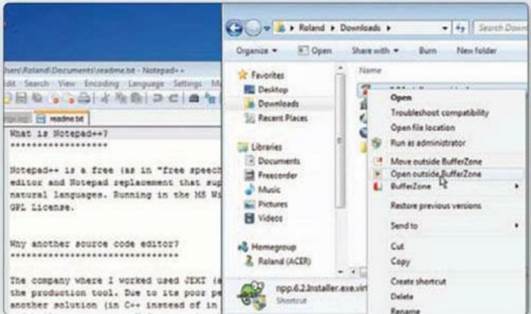
Although the program appears to be
installed and running, it is locked inside BufferZone and can’t access Windows
or your local hard drive. To install the program on your hard drive,
right-click the setup file and choose ‘Open outside BufferZone’.
Step 7
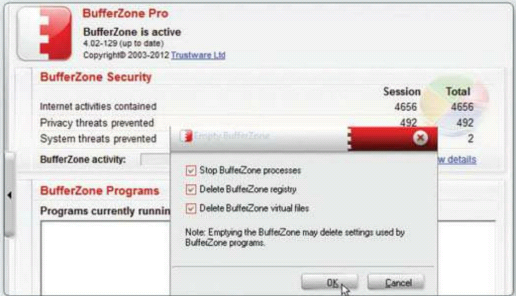
lf you decide not to keep the program you
installed, right-click the BufferZone icon and select Open. Click Empty
BufferZone at the bottom and tick all the options. This clears every file and
every change the program has made.
Step 8
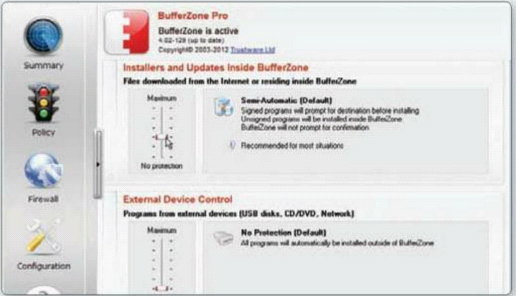
Sliders let you adjust BufferZone’s
leniency when it comes to battening down the PC’s hatches. Select the Policy
tab on the left side of the window, then choose something between Maximum and
No protection for such things as external devices.
Step 9
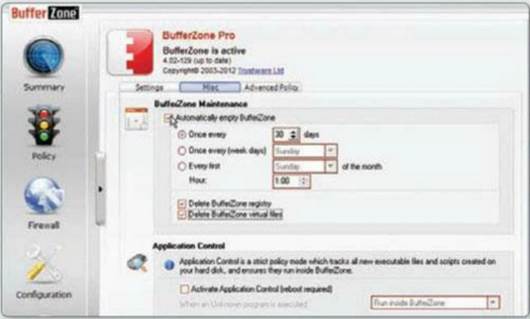
Select the Configuration tab, then choose
the Settings tab. Here you can password-protect BufferZone, perhaps to prevent
a child from changing anything. On the Mise tab, you can schedule automatic
clearing of downloaded files.