Make sure your PC is safe with the
new operating system
Key points
·
Windows 8 has built-in antivirus tools and
anti-spyware protection
·
Smartscreen helps protect the PC from unsafe or
unknown programs
·
Windows access can be protected with a password,
Pin code or picture password
Windows 8 is every bit as secure as earlier
versions of the operating system. But with the new Start screen and revamped
interface, finding old and new security tools can be a challenge. In this Crash
Course, we will explore Windows 8’s security tools to ensure that both your PC
and personal files are completely protected.

Make
sure your PC is safe with the new operating system
Keep viruses at bay
Windows 8 has full built-in protection
against viruses and spyware, thanks to a new version of Windows Defender. This
incorporates the anti-spyware features of previous versions with all the
antivirus capabilities of Microsoft Security Essentials.
An automatic virus scan is performed daily,
but a scan can be run manually at any time. From the Start screen, type
defender then clicks the Windows Defender icon. Choose a scan type (Quick, Full
or Custom) then click Scan now. The Custom scan option allows the user to
choose a specific drive or folder to scan.
By default, all files and programs are
scanned when they are accessed. If a virus is found, a notification appears at
the top right-hand corner of the screen saying ‘Malware Detected’, and the
program will automatically be placed in a protected quarantine area and deleted
after three months.
To turn Defender’s real-time (live)
scanning on or off, click the Settings tab, select ‘Real-time protection’ in
the left-hand list, then tick or un-tick the box labeled ‘Turn on real-time
protection’. We recommend leaving other settings unchanged but, if it needs to
be disabled completely, click Administrator and uncheck the ‘Use Windows
Defender’ box.
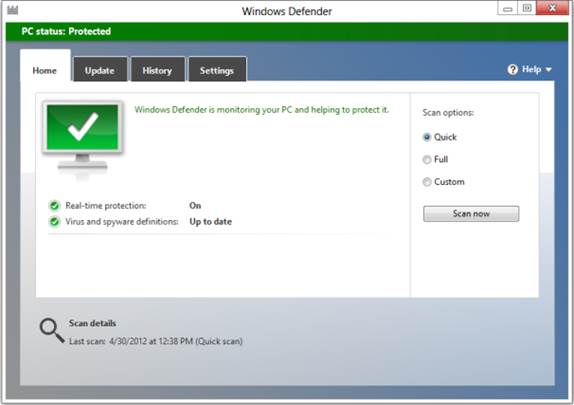
Windows
Defender now includes full antivirus protection
Defender is updated daily but it can be
updated manually by clicking the button on the Update tab. The History tab
shows any recently detected threats, and if a program was mistakenly
identified, it can be restored by checking the box next to its name and
clicking Restore. To delete threats, select Remove All.
Some security features have not changed
much, such as Windows Firewall. This helps prevent other computers on the
internet from connecting to your PC without permission. The firewall works
mostly in the background but, if a new app is installed that needs to accept
connections from the internet, the app will be blocked and a dialogue box will
appear. To allow the app to access the web, click Allow Access. Internet
Explorer 10 has a feature called Smartscreen Filter, which protects users against
known bad programs and malicious websites by checking them against a database.
It is not new, but Windows 8 extends this protection outside the browser with a
feature called Windows Smartscreen, which works regardless of the browser or
antivirus software being used.
If the user tries to open an unsafe or
unrecognized program that was downloaded from the internet, Smartscreen blocks
it with a ‘Windows protected your PC’ warning screen. This can be overridden if
you are sure the program is not malicious – it sometimes incorrectly blocks
lesser-known programs – by clicking ‘More info’, then clicking ‘Run anyway’.
The Action Center
Windows security options are managed in the
Action Center, just as in Windows 7. Open Control Panel (type control panel from
the Start screen, then click to open the Control Panel). Select ‘Review your
computer’s statuses. Click Security to expand the section. If there is a
problem, such as out-of-date antivirus software, it will be highlighted here,
along with instructions on how to fix it. Notifications about security problems
are also shown in the Notification Area of the Taskbar on the old-style Windows
Desktop (click the Desktop tile). Its icon looks like a small flag, just as in
Windows 7, and clicking it shows any alerts along with a link to the Action
Center. For serious problems, the flag will show a red and white cross.
The Action Center also allows User Account
Control (UAC) and Smartscreen settings to be changed. Just as in Windows Vista
and 7, UAC protects users from malicious programs by requiring the user to
approve any changes made to system settings. Do not turn UAC off completely,
but adjust the alert levels using the Change settings link in the User Account
Control section. Smartscreen has three settings: default (where administrator
approval is needed for unrecognized apps), a less-secure mode that just warns
users and disabled.

Security
options are managed in the Action Center
Password protection
User accounts will be explained in detail
in a future Crash Course but, for now, we will explore the new password options
you can use when logging in to Windows. Instead of a password, users can enter
either a four-digit Pin code or the new picture-password feature to sign in to
Windows 8. Both are useful on tablets, where long passwords are a nuisance on a
touch keyboard.
To use a Pin, open the Charms bar (hold
down the Windows key and tap C), click Settings and ‘Change PC settings’.
Select Users, then ‘Create a PIN’. Enter the user password, and then type a Pin
code in the two boxes. In the Pin-entry box, there is an eye icon at the right
edge. Clicking this shows the Pin’s digits temporarily, rather than dots. This
is a useful new feature found in all password-entry boxes in Windows 8, whether
in settings, apps or on web pages, but in Internet Explorer only.

A
Pin code can be used to sign in to your account, instead of a password
When done, click Finish. The password box
at the Windows sign-in screen will now say ‘PIN’. Enter the new Pin to sign in
– there’s no need to press Enter. To use the password instead, click ‘Sign-in
options’ and the key icon.
A picture password involves clicking or
drawing on a photo to sign in. It is intended for touchscreens but can be used
with a mouse. To create one, in the Users section of the PC settings screen
just explored, click ‘Create a picture password’, then enter the user password.
Click Choose picture, browse to a picture, click it then click Open. Click ‘Use
this picture’ then follow the instructions to create three separate gestures
with the mouse (or finger on a touch screen). Only straight lines, circles and
clicks (or taps) are allowed. Repeat when prompted, and then click Finish.
When Windows next starts, repeat the three
gestures (they must be in the same order and direction) on the picture to sign
in. To switch to a normal password or Pin, click ‘Switch to password’. The
sign-in options link will show options for password, Pin and picture password.

Picture
passwords, involving three gestures, are best suited for use on tablets
Jargon buster
Technobabble demystified…
Charms bar:
A tool in Windows 8, used to access common tools such as search and print
Firewall:
Software or hardware that prevents access to a computer over a network, such as
the web.
Notification Area: An area on the bottom-right of the screen that shows programs that
are running.
Operating system: Governs the way hardware and software components work together.
Pin:
Personal Identification Number. Used for cashpoints and online transactions.
Spyware:
Software installed to monitor a computer’s use.
Taskbar: Bar
that runs along the bottom of the screen in Windows.
Tile:
Rectangular elements that make up Windows 8 Start screen.
UAC: User
Account Control. Part of Vista that attempts to protect your PC by verifying
major decisions
Virus: A
computer program made to cause damage to data.