Shutter - Protect your laptop from
thieves
If you’re worried about thieves accessing
your personal information from a stolen laptop, the Shutter utility for Windows
can help block their attempts. The tool shuts down or locks Windows after a
period of inactivity, and can be downloaded for free from www.snipca.com/8864.
To use Shutter, select User Inactive from
the top dropdown menu. Choose how long you want the software to wait and select
an action. The Lock Workstation option is best because it will permanently lock
the thief out of your PC. The flaw with the Shutdown option is that a thief can
interrupt the shutdown process, leaving your files vulnerable. Click Start. The
Status bar at the bottom of the Shutter window will show how long you have been
inactive. This countdown is handy for you but also for anyone wanting to steal
your data. This can be fixed by hiding Shutter. It’s also helpful to set it to
start with Windows.
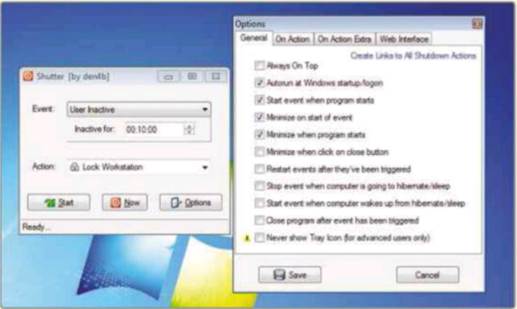
Shutter
locks your laptop after a period of inactivity to prevent thieves stealing data
Close Shutter. Right-click the Shutter icon
and click ‘Run as administrator’. Click Options, select ‘Autorun at Windows
startup/logon’. Click Save and restart Shutter. Return to options and select:
‘Start event when program starts’ ‘Minimize on start of event’, ‘Minimize when
program starts’ and ‘Minimize when click on close button’.
The ultimate safety setting for Shutter is
to tick the ‘Never show Tray Icon’. This makes Shutter virtually invisible. As
it can be tricky to get the Shutter window back, it would be a good idea to
disable the minimize options. Click the close button to hide Shutter when
Windows starts.
Win with your hints
The sender of the Tip of the Fortnight will
win a copy of Honestech VHS to DVD Deluxe worth $90. It includes an adapter to
connect video devices to your PC and software to capture audio and video. Visit
http://uk.honestech.com for more information.
The hint should be around 150 words long and should include a screenshot. Email
entries with your name and address to letters@computeractive.com
or write to our usual address (marking envelopes ‘Hints &Tips’). By
sending a tip, you agree to have it published by Dennis Publishing.
Dropbox - Recover deleted files
Dropbox can recover files that have been
deleted by mistake. Find the folder of the deleted file and click the rubbish
bin next to the search box to show deleted files. Right-click the deleted file
and then click Restore.
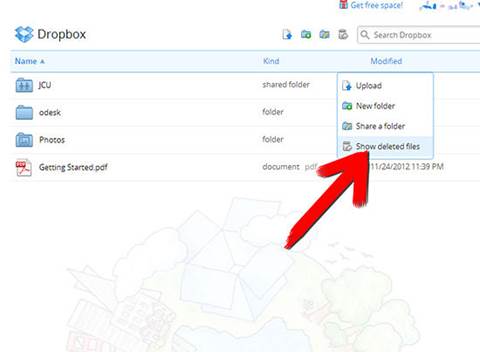
Dropbox
can recover files that have been deleted by mistake
Dropbox keeps past versions of files so you
can recover work that has been edited. Right-click a file and select Previous
Versions. Click one to restore it.
Excel - Create
subtotal formulas
I have a spreadsheet for my insurance
inventory with separate sections for different types of item. Because they are
arranged into Groups (using the icons in the Outline section of the Data tab in
the Ribbon), I can use the Subtotal function to get quick totals for individual
or several groups. This is because the Subtotal function can ignore hidden
cells. This won’t work with cells hidden with the Filter tool. The cells have
to either be hidden manually or with groups.
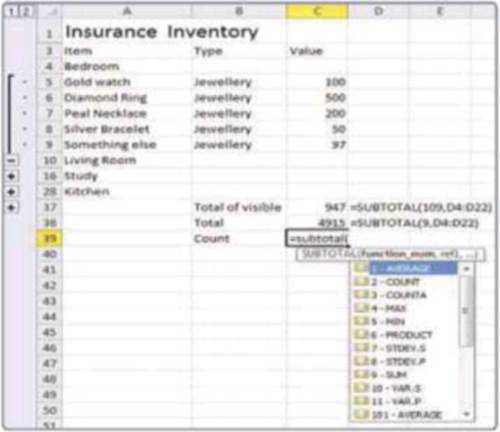
Subtotal
formulas
To calculate the total value of the visible
cells in the range C5 to C36 use the formula =SUBTOTAL(109,C5:C36). The
first number is used to select the kind of function. Three-digit numbers
exclude hidden cells, one-digit numbers include them. Other codes include 1 and
101 for Averages and 2 and 102 for Count. A full list of the different
functions appears as you enter the formula. Find more information at www.snipca.com/8868.
Raspberry Pi - Make remote access easier
If you want to access a Raspberry Pi over a
network, giving it a fixed IP address will save you a lot of time. This is best
set up when the Raspberry Pi is connected to a monitor and keyboard.
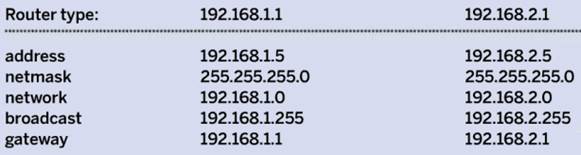
Your router will automatically give out IP
addresses so it needs to be told not to use the address that you give to the
Pi. Consult your router’s manual for exact instructions on changing the range
of addresses used on the DHCP server. I have set my DHCP server to give out
addresses between 192.168.2.20 and 192.168.2.254, leaving 20 fixed addresses I
can use (including one for the router itself).
Raspberry
Pi access
Return to the Raspberry Pi and double-click
LXTerminal. Type cat /etc/ network/interfaces and press enter. This will tell
you the name of your network connection. If you connect with a cable this will
probably be ethO.
Next, type sudo nano /etc/network/
interfaces and press Enter. Move down to the line with your network connection
and replace dhcp with static. Now enter the lines in the blue box above based
on the IP address used by your router.
Press Ctrl and 0 to save the file and Ctrl
and X to quit. Restart the Pi and it should now use the fixed address of
192.168.1.5.
See the discussion on Computeractive’s
forum at www.snipca.com/8865 for
instructions.
Windows 7 - Play sound over HDMI

Windows
7 play sound over HDMI
When you connect your computer to a
television using HDMI, you’ll need to change the audio playback device in
Windows in order to use the HDMI cable for sound as well as video. Once you
have connected the computer and switched on the television, right-click the
Volume Mixer icon in the Notification Area and left-click Playback Devices.
Right-click the box that shows a TV or HDMI device, then left-click ‘Set as
Default Device’. A green tick should appear by this device. Start Windows Media
Player and play some music to test that the audio device is working properly.
It’s probably a good idea to turn the volume on the computer all the way down
to begin with to prevent any nasty surprises.
Microsoft email accounts - Use
two-password authentication
Microsoft has added a security tool to all
its email accounts - Live, Outlook.com and Hotmail - that sends an extra
password to your mobile phone or email address. You’ll need to enter this every
time you sign into a Microsoft Account. This means if someone guesses your main
Microsoft password they still won’t be able to access your account.
Visit www.snipca.com/8888 sign in. A
notification email will be sent to your secondary email account. Copy the code
from the email and click Submit. Confirm the security info. Click ‘Set up
two-step verification’ and then Next. Choose whether to receive a text or call
to your mobile number. A test code will be sent to you.
You’ll get an email confirmation that
explains how to create sign-in details for programs and devices that don’t
support two-step verification, such as Windows Mail.
You can disable these extra passwords for
individual devices, such as your PC at home.
WordPress - Secure your blog
If you use the Word Press blogging software
on your website, you can keep yourself safer from the recent hacks with a
clever plugin that limits unsuccessful login attempts.
WordPress
Log into WordPress and click Plugins. Click
Add New. Search for Limit Login Attempts. Click Install Now, then Activate
Plugin once installation is finished. When four incorrect attempts are made in
a row the site will disable login requests for 20 minutes. For more information
see www.snipca.com/8869.
KeePass - Read passwords more easily
KeePass
If you find it hard to read passwords in
the KeePass manager, you can adjust the font so it’s easier to read. Click the
Tools menu and then Options. Click the Select Password Font button at the
bottom right. Choose a new font, style and size and then click OK. Don’t make
it larger than 18 point or the text won’t display properly. Consolas is a good
choice as its zero and letter 0 are easy to tell apart.