What they are & what you can do
about them
Human resources personnel follow the
company's security protocol to the letter. A very strong 15-character password
is used to log on to the cloud provider's server through its website. Before
sensitive employee data is uploaded to the cloud server, the security software
has flagged no warnings about the Web interface. The URL address begins with
"https," indicating that either the TLS (Transport Layer Security)
or SSL (Secure Sockets Layer) protocol is encrypting the connection. But what
the HR person does not know as the data uploads is that a malicious attacker is
at the other end of the connection, seeking to broker the information he
gathers to identity thieves. The attacker has also received the encryption keys
from HR to access other company data on the cloud provider's servers for an
even bigger score.
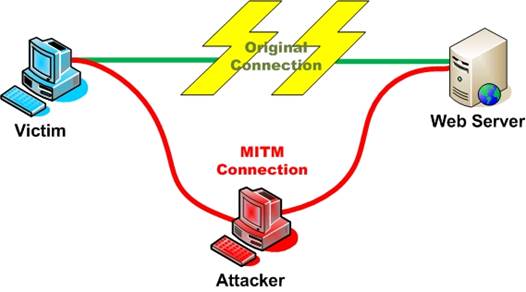
An
attacker, like the TG group, desires to covert the DNS system to send all
internet traffic to the legitimate site to its own site.
The next day, after attempting to log on to
the storage provider's Web interface and calling to report the problem, the
hapless HR employee discovers that all employee records on the cloud servers
have been stolen. Because the employee had followed security procedures, there
appears to be no take-away lesson from this catastrophe.
Attack mechanics
This scenario illustrates one of many
possible types of MITM (man-in-the-middle) attacks. In general, a MITM attack
involves an attacker who tricks two parties into believing they are
communicating directly with each other, when in fact all communications are
passing through the attacker. What is particularly tricky about MITM attacks is
that there is no evidence of this "middleman" as far as the legitimate
users are concerned. Communications look as though they are encrypted, with
"https" in the browser URL and security software indicating a
protected connection. "Encryption just means that the pipe is
secure," says Bruce Schneier, an independent security expert and author
(www.schneier.com). "It doesn't indicate [whom] you are talking to. You
could be talking to Doctor Doom."
Other examples of MITM attacks are a
key-logger program that intercepts data, or a phishing scheme through which an
unsuspecting user uploads sensitive data to a bogus website. However, a common
type of MITM attack takes advantage of website vulnerabilities, when an
attacker's program passes the authentication test and establishes a connection
between two endpoints. A security hole in a website, for example, can be
hijacked with a simple Java command or even through HTML text with the help of
rogue software to lay the groundwork for the attack.
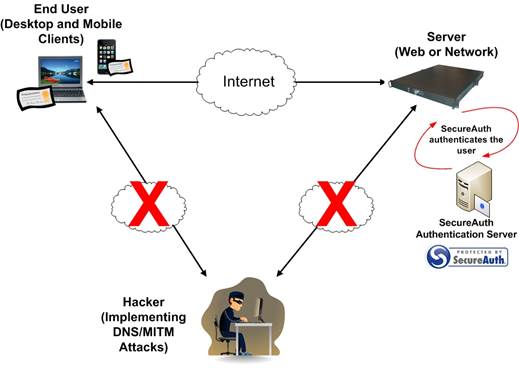
SecureAuth
mitigates the DNS/MITM attacks by creating and distributing (and revoking)
client side certificates for the end users
"A very prevalent type of MITM attack
is when someone hijacks a Web connection," says Anton Chuvakin, an analyst
for Gartner (www.gartner.com). "It executes a simple 'view your stocks
online' message to you and then executes a
'sell-your-stock-and-then-send-some-money-to-Estonia' command to your
bank."
Encryption isn’t everything
The main function of encryption is to
create virtually impenetrable tunnels through which data transfers can occur.
Authentication protocols also play a key role to ensure that the person or computer
on the other end of a connection is the right one. But while encryption does
indeed secure the connection so that it can be virtually impossible for a
third-party intruder to decipher the data without the encryption keys, it does
not guarantee authentication protection either, even though that is one of its
functions. Still, using encryption as a means to thwart MITM attacks is
essential.
"People break in through windows, but
you still need to trust door locks," Schneier says. "Encryption will
not magically keep you safe, just like a door lock will not magically keep you
safe. It is a security tool [to use with other security tools]."
Cloud worry
A MITM attack can compromise financial records,
customer or employee information, or other sensitive data, of course. But when
all of this data is collectively pooled and uploaded through a single
connection to a cloud provider, the potential threat can become very
significant. A cloud provider's user interface is very often accessed through
a Web connection, making cloud storage even more vulnerable, since MITM attacks
largely involve Web browsers.
"If you use the cloud, there is a lot
at stake if you lose access to [your cloud data due to] a MITM attack,"
Chuvakin says. "It is one thing for someone to hijack access to a Web
forum, but it is something else altogether to lose access to all of your
sensitive cloud data."
Do what you can
Beyond watching out for security warnings
about invalid certificates and making sure there is an "https" in the
URL (indicating a secure connection), there is, unfortunately, little the
average non-expert user can do alone to thwart MITM attacks. Some published
reports say users should consider the possibility of a potential MITM threat if
they notice their computer is running slower than usual, for example. However,
anything from a faulty hard drive to a software glitch could slow down a PC.
Users should also be on the lookout for
warnings and alerts from security software that flags unsecured Web pages or
connections. "If your browser says the certificate is invalid, then don't
go there, especially if it is a sensitive site," Chuvakin says.
You need to also watch for basic common sense
signs of a MITM or any other kind of attack. "Just paying attention is
good," Schneier says. "I mean, if you look at your bank statement and
you sent $7 million to the Russian mafia, [then something is wrong]."
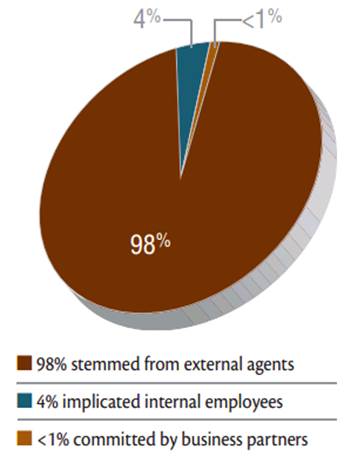
Source:
Verizon data breach investigations report
The best an enterprise can do to ward off
MITM attacks is to keep software and anti-malware updates current and to make
sure that security software and appliances are properly configured and
monitored. While MITM attacks can be understood by the layperson on a
conceptual level, assessing the intricacies of the attacks and understanding
specific vulnerabilities requires the skills and talents of a professional.
"I would hire somebody that knows what
they are doing and avoid advice in newspaper articles," Schneier says.
"Any specific advice you read about MITM is incomplete and probably
wrong, because the subject is too complicated."
Sources of MITM Attacks
Man in the middle attacks fall under the
external agent category, which represent the vast majority of data breach
incidents.