Encrypting files just highlights the fact
that you have something to hide. We show how steganography is better
Take a moment to think about all the
different activities you carry out on your computer. You send and receive
emails, access online banks and pay bills, shop at various online stores, log
in to countless websites and services online, store notes, financial
information, personal details, and the list goes on. What would happen if your
computer was stolen or if someone else gained access to it? The thief would
have access to everything and it could have serious consequences.
Security is not something we tend to worry
about until there is actually a problem. We often use minimal security until
something bad happens either to us or to someone close to us. Then we realize
that actually we have little protection and something must be done either to
prevent it happening again or to us. Wouldn't it be better to boost the
security now rather than after a thief or hacker has stolen your files?
There are many ways to improve the security
of your PC and in this article we will look at one particular method called
steganography This is a method of concealing information so that others cannot
access it. You're probably familiar with cryptography, which is a way of
turning information into a secret code that is hard or even impossible to
decrypt. Steganography is not cryptography, but the two are often used together
to enhance security.
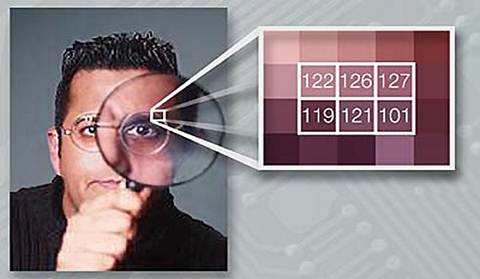
Steganography hides information within
other information. A simple example often used in spy books and movies is the
microdot, which looks like a full-stop printed on a page of text, yet it
contains secret information that the spy can access using a microscope or some
other gadget. Microdots are real and they were actually used in the Second
World War. Invisible ink is another example of steganography and the paper used
to write the message could be blank or the invisible writing could be between
the lines of whatever text is on the page or in the margins.
These are recent examples, but
steganography is centuries old, and there are stories from ancient Greece about
couriers having messages tattooed on their shaved heads and then when their
hair grew back it was hidden. It must have taken weeks or months to send a
message, which wouldn't be much good in today's world. We need something
faster, easier and reusable.
Computers have revolutionized
steganography, so thankfully there's no longer any need to tattoo a message on
your slave's head. There are now very simple utilities, many of which are free,
which enable you to hide all manner of information within other information.
For example, it's possible to hide a text message within a digital camera photo
or an audio file that is impossible to detect. Only you or someone you reveal
the secret access code to can read the text. It's even possible to store one
photo within another photo, a whole document or audio file within another audio
file or photo.
There are many applications for this and to
give one simple example, you could store your online banking passwords within
your holiday snaps or within your favorite music track. Your photos would not
look any different and you could listen to the music just as you always have.
Who would suspect that they contained secret information? Any encrypted file on
the disk drive obviously contains private information and a thief that gained
access to your computer would try to crack the coding, but they wouldn't know
which of your digital camera photos or music albums contained secret
information. It's doubtful they would even consider the possibility.
“Any
files, folders, messages and other information you want to hide can be hidden
using steganography”
Any files, folders, messages and other
information you want to hide can be hidden using steganography. They can be
stored on your computer for your own use or sent by email or instant messaging
to someone else you want to give the information to. For example, if you wanted
to send someone a password to access some shared online service or to give
someone your bank details so they can send you money, instead of sending it
using plain text in an email, which anyone could read, or encrypting it, which
is hard to crack but obviously contains something secret, you could send them a
photo. The recipient could then extract the information from the photo and
anyone that intercepted the email would never know that you were exchanging
information with the person. It would look like you were sending them a photo
of your pet dog or something.